Cybersecurity isn’t about completely avoiding an attack – that isn’t feasible. Today, security aims to build resilience. A resilient business can withstand and attack and continue operating in adverse conditions.
Mastering Cyber Resilience: Using a Layered Security Approach
Understanding Cyber Resilience:
Cyber resilience isn’t just putting up thick barriers; it’s about cultivating a mindset and framework that enable organizations to adapt, respond, and recover swiftly from cyber incidents. At its core, cyber resilience entails a proactive approach that blends structural and situational awareness with robust incident response mechanisms.
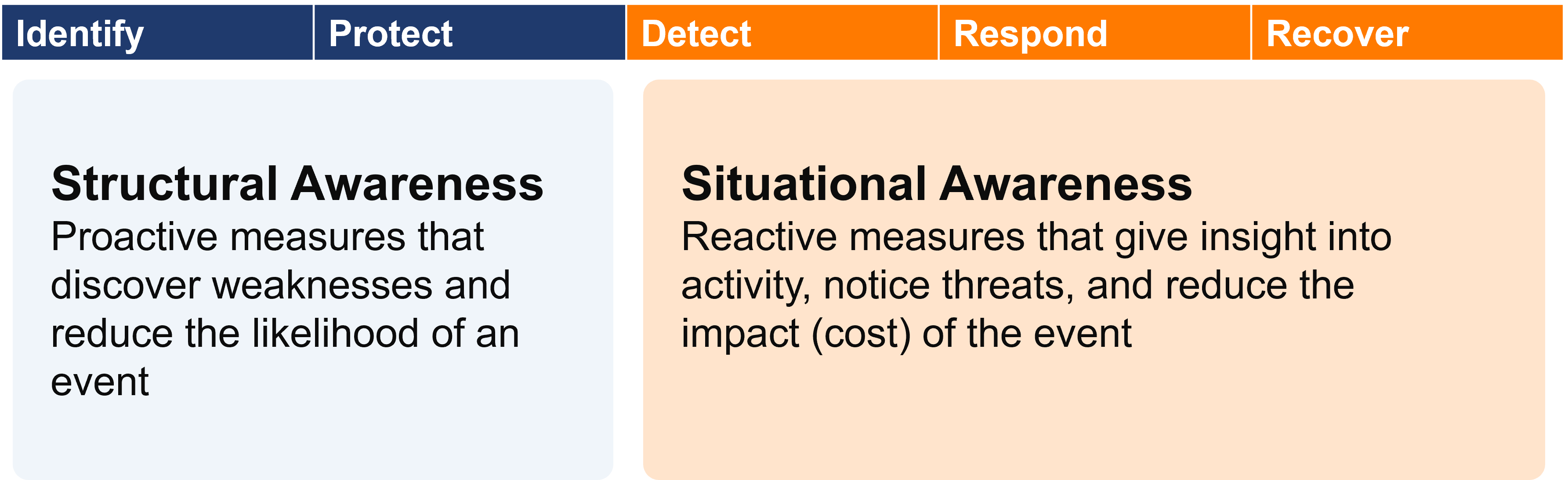
Structural Awareness:
The foundation of cyber resilience lies in structural awareness – a comprehensive understanding of your organization’s digital assets. From workstations and servers to cloud infrastructure and applications, you must be aware of every aspect of your digital ecosystem. This approach aligns with the National Institute of Standards and Technology (NIST) Cybersecurity Framework, which emphasizes the importance of identifying, protecting, detecting, responding to, and recovering from cyber threats.
Situational Awareness:
Situational awareness refers to incident response – your organization’s ability to recognize potential threats in real-time and swiftly respond to mitigate damage.
Incident response plans should be clear, but dynamic. That means that each step of the response is clearly outlined, but it is flexible enough to fit a wide variety of security incidents.
The Role of Technology and People:
Achieving cyber resilience demands that you have the right technology in-place, and the human expertise to manage it.
While technological solutions provide the foundation for threat detection and mitigation, human intuition and experience are indispensable for interpreting complex threat landscapes and orchestrating effective responses.
Implementing a Layered Defense:
You might choose to implement a single tool that offers partial coverage for certain security needs. However, it is crucial to recognize that no single tool can provide protection for all aspects of cybersecurity. This is where a layered defense strategy becomes essential.
Embrace the notion that while one tool may not cover everything, leveraging multiple complementary tools is key. By doing so, the probability of detecting or blocking threats significantly increases across various layers of defense.
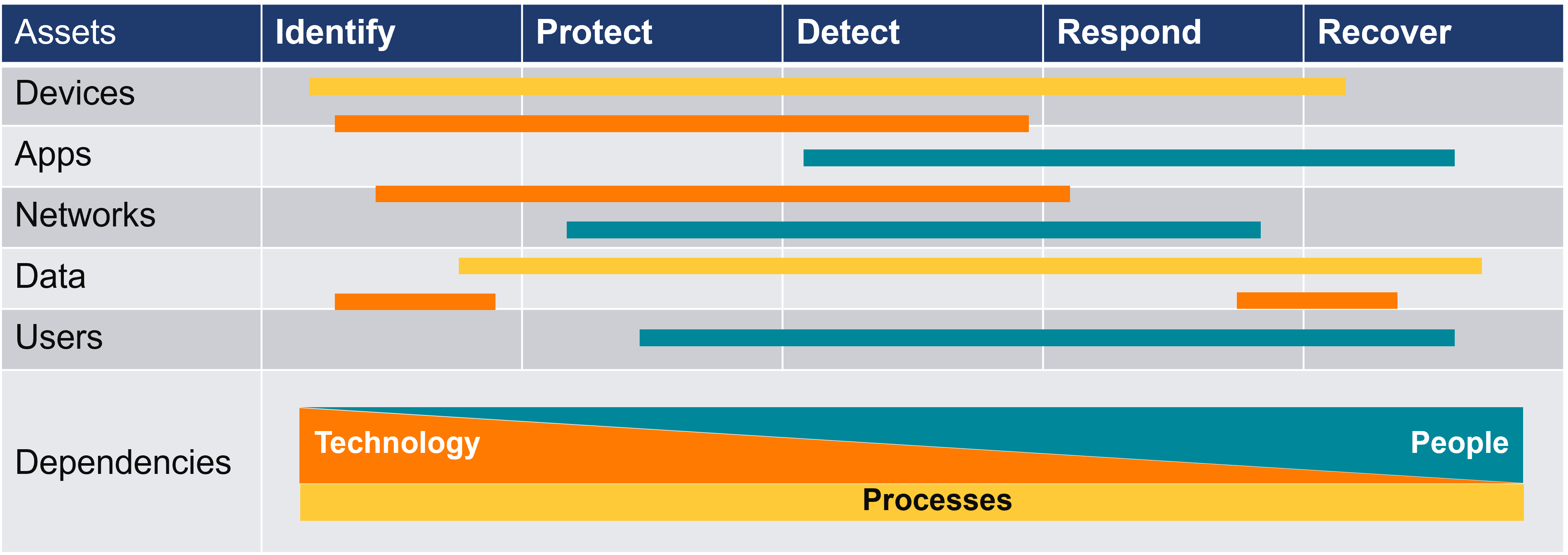
By combining people, processes, and technologies, organizations can assess where their risks lie, identify critical assets requiring protection, and determine the most effective methods for safeguarding them while also preparing for potential responses. Instead of relying solely on a singular solution, it’s imperative for organizations to adopt a multifaceted approach that integrates diverse security measures.

Fundamental Layers to Consider:
When evaluating your cybersecurity posture, consider these layers prior to an attack:
Technology
- Air-gapped Data Backup
- E-Mail & Internet Threat Filtering
- Managed Detection & Response (MDR)
- Conditional Multi-Factor Authentication
- Security Information & Event Management (SIEM)
- External Vulnerability Scanning
People
- IT Team
- Cybersecurity Insurer
- Attorney
- Internal security response team
- Security Operations Center (SOC)
Processes
- Incident Response Plan
Remember, cybersecurity resilience is about being prepared and proactive. By implementing the right tools, training your team, and having clear protocols in place, you can effectively mitigate cyber risks and safeguard your organization’s assets.
Watch the Full Webinar
Experts from Buchanan, Higginbotham, and Aldridge give an update on today’s cyber threats, and why it is only a matter of time before your business will be breached. If you start planning for an attack today – thinking through your risks and implementing the right risk management tools, you can survive any cyberattack. Watch the full Prepare, Respond, & Recover webinar to see how you can start planning.
