The Most Common “Breach” Today
Email compromise is a growing threat that poses a significant risk to organizations worldwide. Attackers target individuals and organizations to gain access to sensitive data, financial information, and intellectual property. The impact of a successful email compromise can be devastating, including financial losses, damage to reputation, and legal ramifications.
As technology advances, so do the tactics and techniques of threat actors. They use sophisticated methods to gain access to email accounts, such as phishing attacks and social engineering tactics. They often masquerade as legitimate senders, leading unsuspecting users to click on links or download attachments that contain malware.
Once they gain access to an email account, threat actors can read, send, and delete messages without the user’s knowledge. They can use the information they obtain to perpetrate further attacks, steal data, and commit financial fraud. They can even alter or delete critical emails, compromising the integrity of the mailbox contents.
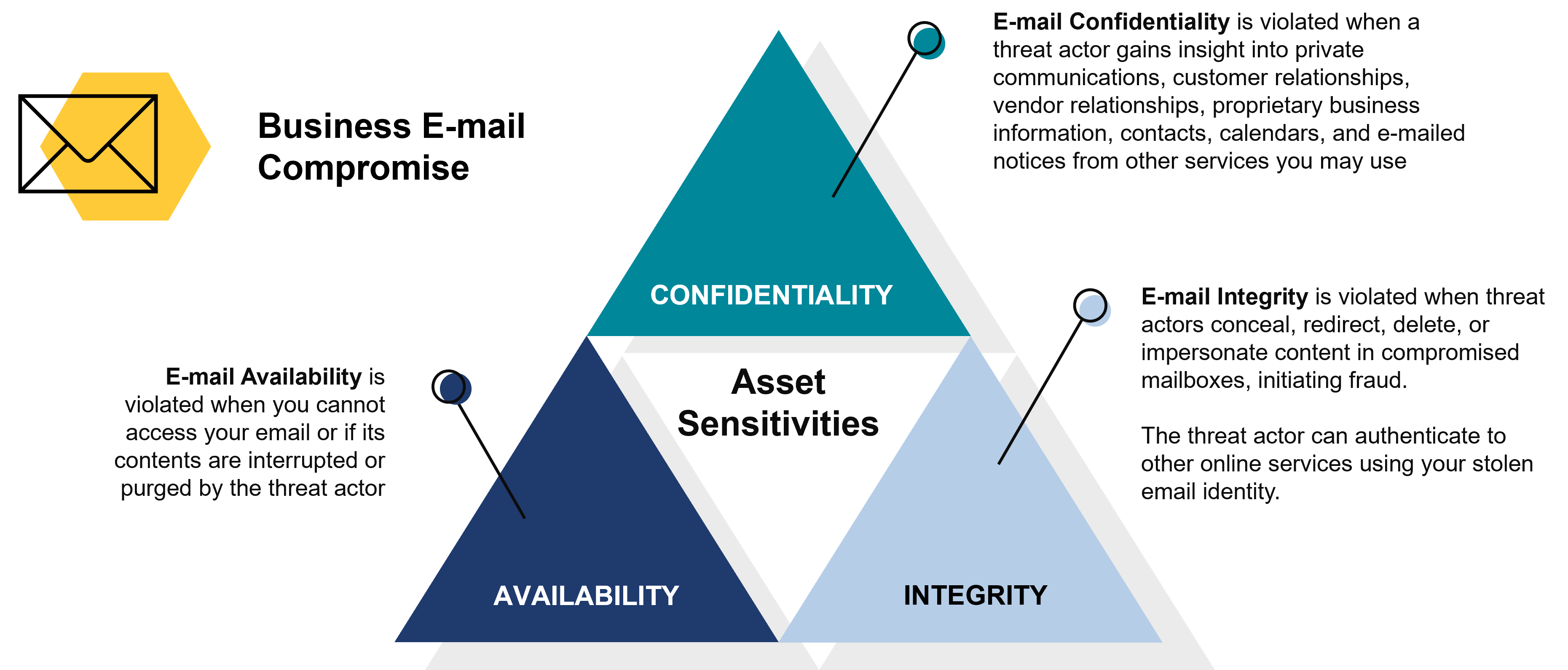
Asset Sensitivities – CIA Triangle
When it comes to email compromise, the three main asset sensitivities are confidentiality, integrity, and availability. What is the difference?
E-mail Confidentiality
Confidentiality of email is breached when a malicious actor gains access to private communications, customer and vendor relationships, proprietary business information, contacts, calendars, and email notifications from other services you may use. It is important to maintain email confidentiality as it helps to protect sensitive information, such as trade secrets, financial information, and personal information from falling into the wrong hands. If you’re in a regulated industry, breaches in confidentiality can result in legal and financial consequences.
E-mail Integrity
The integrity of an email is compromised when threat actors conceal, redirect, delete, or impersonate content in compromised mailboxes, leading to fraudulent activities. These threat actors can even use your stolen email identity to authenticate themselves to other online services. It is vital to maintain email integrity to ensure that the content of emails remains unaltered and trustworthy. Breaches in email integrity can result in financial losses, identity theft, and other forms of fraud. In addition, email is often used for sensitive communication, including business and personal matters, which makes maintaining its integrity even more crucial.
E-mail Availability
Availability of email is compromised when an individual is unable to access their email or when its contents are disrupted or deleted. Maintaining email availability is critical to ensure that individuals and organizations can communicate and access important information. Breaches in email availability can result in missed business opportunities, delayed communication, and even legal consequences. In addition, email is often relied upon for time-sensitive communication, making availability even more important.
Organizations must take proactive measures to protect their email systems and users from email compromise attacks. This includes implementing strong passwords, multi-factor authentication, and security awareness training for employees. Organizations should also implement tools to monitor and detect unusual activity within email accounts, such as the use of email security solutions that can detect and prevent unauthorized access.
How to help prevent business e-mail compromise:
- Employee Training: Educating employees on the importance of cybersecurity and how to recognize and report suspicious activity can help prevent BEC attacks.
- Two-factor authentication: Requiring two-factor authentication can add an extra layer of security to email accounts, making it harder for attackers to gain unauthorized access.
- Email filtering: Implementing email filters that scan incoming and outgoing emails for signs of phishing and other malicious activity can help prevent BEC attacks.
- Password management: Encouraging employees to use strong passwords and implement password management tools can prevent BEC attacks that exploit weak or reused passwords.
- Vendor management: Managing vendors’ access to the organization’s email systems and ensuring they adhere to security best practices can prevent BEC attacks that exploit third-party access.
- Multi-level approval: Implementing multi-level approval processes for financial transactions and other sensitive activities such as a change in a vendor’s bank routing information can prevent fraud from a BEC compromise.
By implementing these preventative measures, organizations can significantly reduce their risk of falling victim to BEC attacks.
Email compromise is a significant and growing threat that organizations must take seriously. By implementing best practices and security measures, organizations can reduce the risk of email compromise and protect their valuable data. The consequences of inaction can be dire, leaving organizations vulnerable to financial losses, legal repercussions, and damage to their reputation.
Watch the full webinar
Learn about today’s threats, how to effectively manage your cyber risk, and 4 steps you can take today to prepare your business from what’s coming next: 2023 State of Cybersecurity | You Will Be Breached







