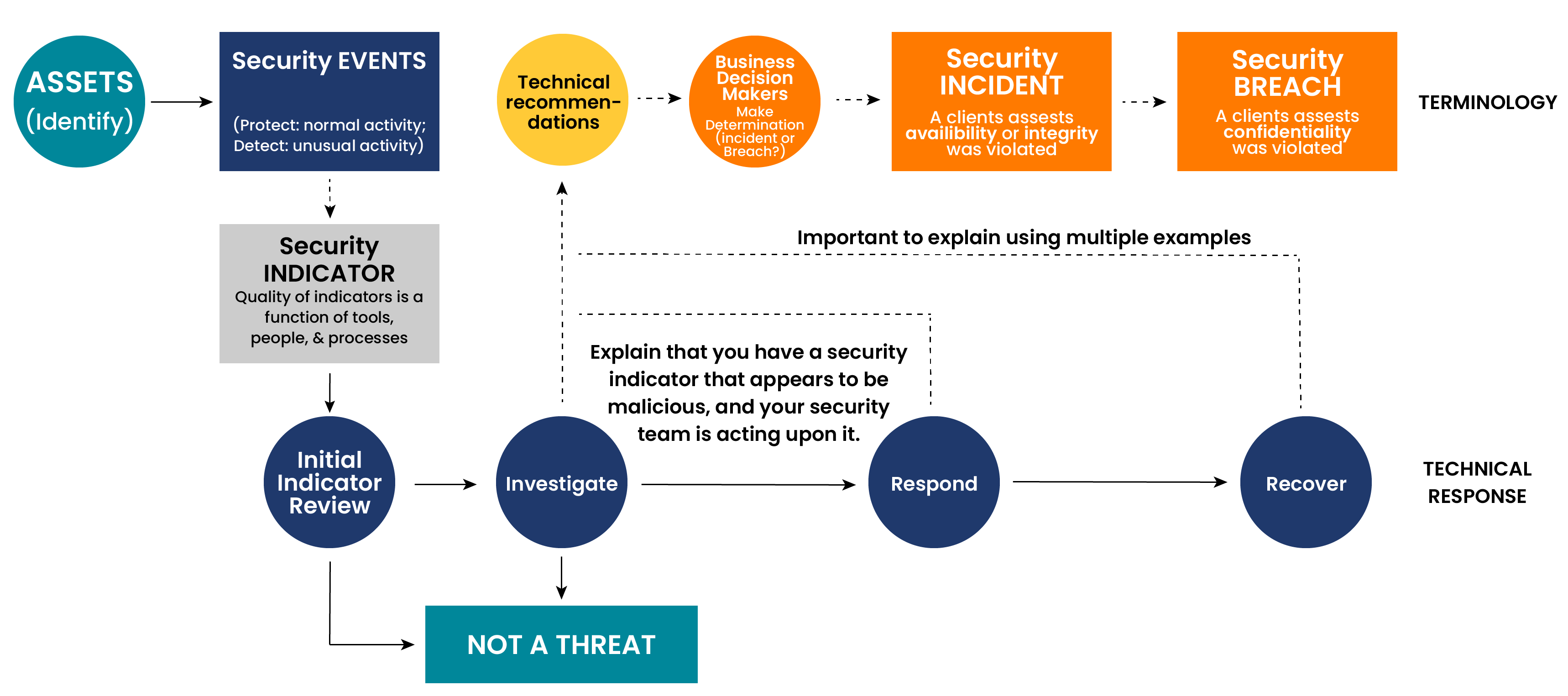
It’s essential to grasp the nuances between security events, indicators, incidents, and breaches. Often, these terms are used interchangeably, but understanding the distinction is key. If your team throws out the word “security incident” or “breach” loosely then you are opening yourself up to unnecessary liability.
Events, Incidents, and Breaches: Understanding Cybersecurity Terminology
Security Events: Normalcy in Action
Security events encompass a wide range of routine activities within digital systems. These events serve as the baseline for cybersecurity monitoring and analysis. Every time a user logs into a system, accesses content, or modifies data, it constitutes a security event.
Essentially, any activity that leaves a digital footprint can be considered a security event. These events are constant and are typically logged for monitoring purposes. Recognizing and understanding security events is essential for establishing a baseline of normal behavior, which serves as a reference point for identifying anomalies and potential security threats.
Identifying Security Indicators
Security indicators play a critical role in detecting potential threats and vulnerabilities. These indicators are abnormalities from normal system behavior that may signify a security risk.
These abnormalities could include things such as:
- Unusual login patterns
- Unauthorized access attempts
- Suspicious network traffic
Recognizing these indicators requires a deep understanding of the organization’s digital environment and the ability to distinguish between routine activities and potential threats. Security teams leverage monitoring tools and technologies to detect and analyze these indicators, enabling them to respond promptly to emerging threats.
From Event to Incident or Breach: The Response Process
While security events are a regular part of digital operations, not all events escalate to security incidents. Security incidents occur when a security event poses a significant risk to the organization’s confidentiality, integrity, or availability of their data and systems.
If your security team receives an indicator, it initiates your technical response process. This technical response process involves:
- Assessing the severity of the event
- Containing the threat
- Investigating the cause
- Implementing measures to mitigate the impact
Leadership involvement is crucial in determining the classification of an event as an incident, as it has legal or compliance consequences for the organization. The security team should investigate indicators and present their findings to leadership. Leadership then determines if the event is a true security incident, or a security breach.

The Importance of Terminology
Precise terminology is not only vital for internal communication but also when interacting with customers. Misuse or misinterpretation of terms like “incident” and “breach” can lead to confusion and miscommunication, potentially harming customer relationships and even legal standing.
Definitions:
- Security Event: A security-related activity identified and recorded through monitoring systems.
- Indicators (Indicators of Compromise (IOCs)): Forensic data pieces identifying potentially malicious activity on systems or networks.
- Incident (Cyber-Incident/Security-Incident): Confirmed malicious action by a threat actor, triggered by suspicious activity.
- Breach (Data Breach): Unauthorized access to sensitive or confidential information.
If there are uncertainties about discussing these terms with customers, seeking guidance from cybersecurity experts can ensure accurate communication and maintain trust.
Implementing Incident Response Plans
Every organization should have a robust incident response plan in place. This plan outlines how to handle security incidents, who is responsible, and the steps to mitigate damage and restore normal operations. Importantly, the incident response plan should kick in as soon as there’s suspicion of a potential security incident, allowing for swift and coordinated action.
Incident response plans should be regularly reviewed, tested, and updated to ensure their effectiveness in addressing evolving cybersecurity threats. By having a robust incident response plan in place, organizations can minimize the impact of security incidents and maintain operational resilience.
Preparation and Resilience
Maintaining resilience in the face of cybersecurity threats requires proactive measures. Mobilizing expertise and resources at the earliest indication of a potential incident is crucial for minimizing damage and returning to normalcy swiftly.
Maintaining resilience in the face of cybersecurity threats requires proactive measures and readiness to respond effectively to incidents. This includes:
- Investing in cybersecurity training and awareness programs for employees
- Implementing robust security controls and monitoring systems
- Establishing partnerships with cybersecurity experts and incident response vendors
Organizations should also conduct regular risk assessments and vulnerability scans to identify potential weaknesses in their systems and processes. By continuously improving their cybersecurity posture and preparedness, organizations can enhance their resilience to cyber threats and minimize the risk of disruption to their operations.
By adopting clear terminology and implementing robust incident response plans, organizations can enhance their resilience and effectively mitigate cyber threats.
Watch the Full Webinar
Experts from Buchanan, Higginbotham, and Aldridge give an update on today’s cyber threats, and why it is only a matter of time before your business will be breached. If you start planning for an attack today – thinking through your risks and implementing the right risk management tools, you can survive any cyberattack. Watch the full Prepare, Respond, & Recover webinar to see how you can start planning.







