By now, you most likely know there has been an increase in the number of cyberattacks on small and midsized businesses, but you may not know the level of sophistication many cybercriminals have when it comes to planning and executing attacks.
We break down the four-part process cybercriminals go through when planning and executing a cyber attack.
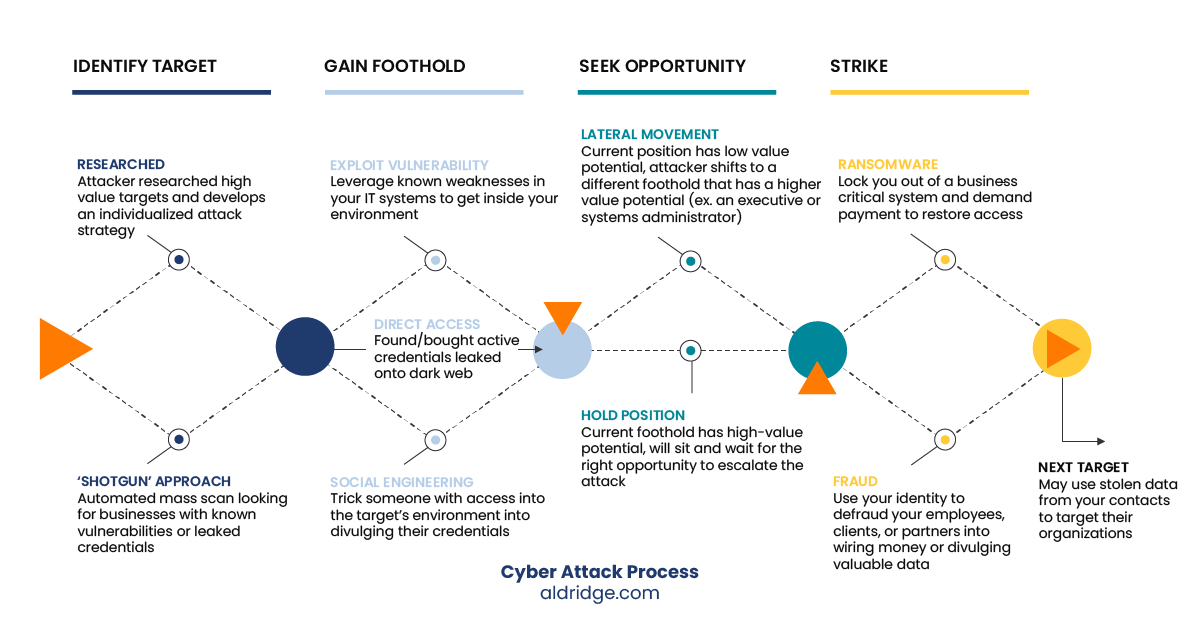
Identify Target
When it comes to identifying what organization or individuals to target, bad actors utilize two approaches:
Researched: this is when a bad actor identifies a high-value target and plans a specific, highly individualized attack.
Shotgun: In this approach, the criminal uses automated software to launch a low sophistication attack over a large number of targets, hoping a small percentage of them are successful.
Gain Foothold
If the attack is successful, the bad actor will gain a foothold within your company’s network. There are multiple methods a cyber criminal could use to gain access to your environment:
- They might have bought active credentials (username & password) off the dark web.
- They may have used social engineering to trick one of your employees into divulging their credentials or installing malware on their computer.
- They may have leveraged a software exploit before the manufacturers even knew about the vulnerability (e.g. Log4j).
Seek Opportunity
Regardless of how the bad actor gained access, they’ve now got a foothold in your systems and can access privileged data. Depending on the goals and sophistication of the bad actor, they may escalate the attack right away or they may take some time to monitor your environment to identify a higher-value exploit (e.g. compromising the account of an executive or an IT administrator)
Strike
Once the value of the target is high enough or their window of opportunity is closing, the bad actor takes action. This could result in financial fraud, relationship exploits, ransomware, and/or disruption to your business. The process can continue using each compromise as a discovery point to start a new string of related compromises to your associates, partners, customers, and to your vendors.
Cybersecurity is a layered approach to anticipate, prevent, detect and respond to each of the steps in this process. Learn about our IT Security services and how we can help lessen your risk of falling victim to one of these cybercriminals.
Hear our CIO, Chad Hiatt, talk about this topic from a recent webinar.







