Cybersecurity is on every business leader’s mind, but what are they actually thinking about? To answer that question, we conducted a survey of over 100 small business leaders and here is what we learned.
Where are you on your ‘Security Journey’?
The ‘Security Journey’ refers to the process of building an overall security strategy that fully controls your risk based on your organization’s risk appetite. Organizations that are far along on their security journey, have identified all of their major risks and have implemented a plan to protect their most critical vulnerabilities. They have thought through attack scenarios and have procedures in-place to recover from all common threats. They have an ongoing process to evaluate and refine their security strategy based on new threats and tools.
Here is where our small business leaders see themselves on this journey:
-
- We have a mature cybersecurity strategy that addresses our major risks: 16.22%
- We have a cybersecurity plan and are working towards where we need to be: 21.62%
- We have some security tools but no comprehensive plan or strategy: 56.76%
- We are just beginning to think about security but haven’t taken any action yet: 1.35%
- We have not seriously discussed security: 4.05%
Based on these results, only 38% of small businesses have begun their security journey in earnest. The majority of businesses are still struggling to put all the pieces together and develop a strategy. If you’re part of the 62% of businesses that are struggling to put your security strategy together, check out 3 steps to building an effective security strategy.
Which of these cybersecurity tools are you familiar with? Which do you use?
There are so many new security tools and acronyms being thrown around that it can be hard to keep track of it all. We came up with a list of common security elements to gauge how familiar most executives are with these tools and how many have implemented them within their own organizations.
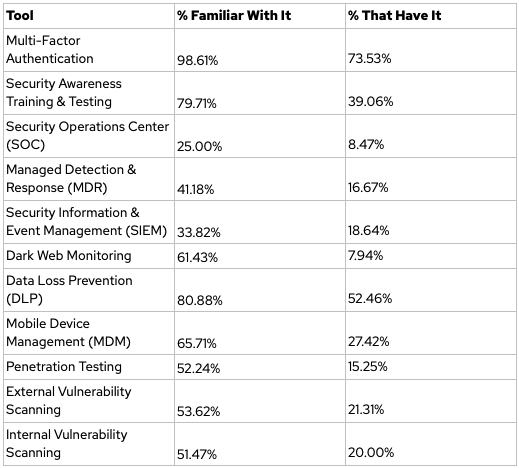
The good:
-
- It is reassuring to see that at least 75% of businesses utilize Multi-Factor Authentication (MFA). MFA is an extremely efficient way to protect your business from unauthorized account access.
- In general, there is a good level of awareness among executives on most of these tools – even if they aren’t implemented yet.
The bad:
-
- Only 39% of businesses are utilizing Security Awareness Training, this number is far too low. The vast majority of cyber attacks utilize social engineering; your team needs to be educated on how to spot a phishing attack. You need to conduct an ongoing simulated phishing attack campaign to instill a baseline level of vigilance in your team towards suspicious emails. Mock attacks are very effective because no one wants to fail the test and get enrolled in even more security awareness training courses!
- Managed Detection & Recovery (MDR) and External Vulnerability Scanning are not being utilized anywhere near as much as they should be. These elements are quickly becoming core security components and need to be implemented as soon as possible.
Our recommendations:
-
- If you have not done so, you need to implement: MFA, MDR, Security Awareness Training and Testing, and regularly conduct external vulnerability scans & dark web scans. These are core security elements and implementing them all is a good goal for businesses starting their security journey. Many of these elements are relatively inexpensive and straightforward to implement.
- Keep an eye on SOC + SIEM, MDM, internal vulnerability scanning, and pen testing. These are more advanced security elements and businesses just starting out on security likely aren’t ready to implement them. Over time we expect these tools to become necessary for all businesses so it is important to at least be aware of them.
47% of small businesses have cyber insurance.
You will eventually get breached, cyber insurance is how you control your recovery costs and manage your risk. Insurance carriers are the ones driving the adoption of security tools and policies by raising the requirements to get coverage.
Related: 2022 SMB Cyber Insurance Stats
What motivates you to implement new technology?
We all know that implementing new technology is a pain. Unfortunately, raising your security posture involves many tool and process implementations. To better understand how business leaders feel about new technology in general we asked two questions:
- Which of the following best describes your organization’s attitude towards adopting new technology?
-
- We want the latest technology to set us apart from our competitors: 12.68%
- We want to keep up with our industry: 76.06%
- We do not want to adopt new technology unless we are forced to: 11.27%
-
Unsurprisingly, most small businesses don’t desire to be on the cutting edge of technology – they just don’t want to be behind. Now that we’re seeing rising security requirements in insurance, compliance, and MSA’s businesses are scrambling to keep-up. This is further supported by the second question, where improving security and compliance obligations were among the top reasons for new tech implementations:
- What factors drive you to implement new technology? (more than one answer could be chosen).
-
- Improve security & reduce risk: 76.06%
- Improve the quality of life for current employees: 54.93%
- Compliance requirements: 50.7%
- Increase efficiency to avoid adding headcount: 46.48%
- External pressure (peers, partners, or clients): 22.54%
- Attract top talent: 19.72%
- Increase efficiency to reduce headcount: 19.72%
- Other: 9.86%
Bring your questionnaire to your IT team at least 90 days before it is due so that there is enough time to do it right.
Our Takeaway
In the past, cybersecurity was seen as something only companies in highly regulated industries and enterprise-level organizations had to worry about. Many small businesses are finding out the hard way that this isn’t true. Small businesses are seen as a soft target and are increasingly being targeted by cyber criminals. The main takeaway from this survey is that small business leaders are becoming aware that security is important, but there is still a lot of work that needs to be done to get their security to where it needs to be.







