If you get caught in a business email compromise, the process can start a new string of related attacks on your associates, partners, customers, and vendors. Financial fraud, relationship exploits, ransomware, and business disruption are all likely outcomes of an email compromise.
An effective security solution can disrupt an email compromise by anticipating, detecting, and responding to each step of the attack. In this post, we explain what the attack process might look like for an email compromise and financial fraud event to help you avoid falling victim.
What Is A Phishing Email?
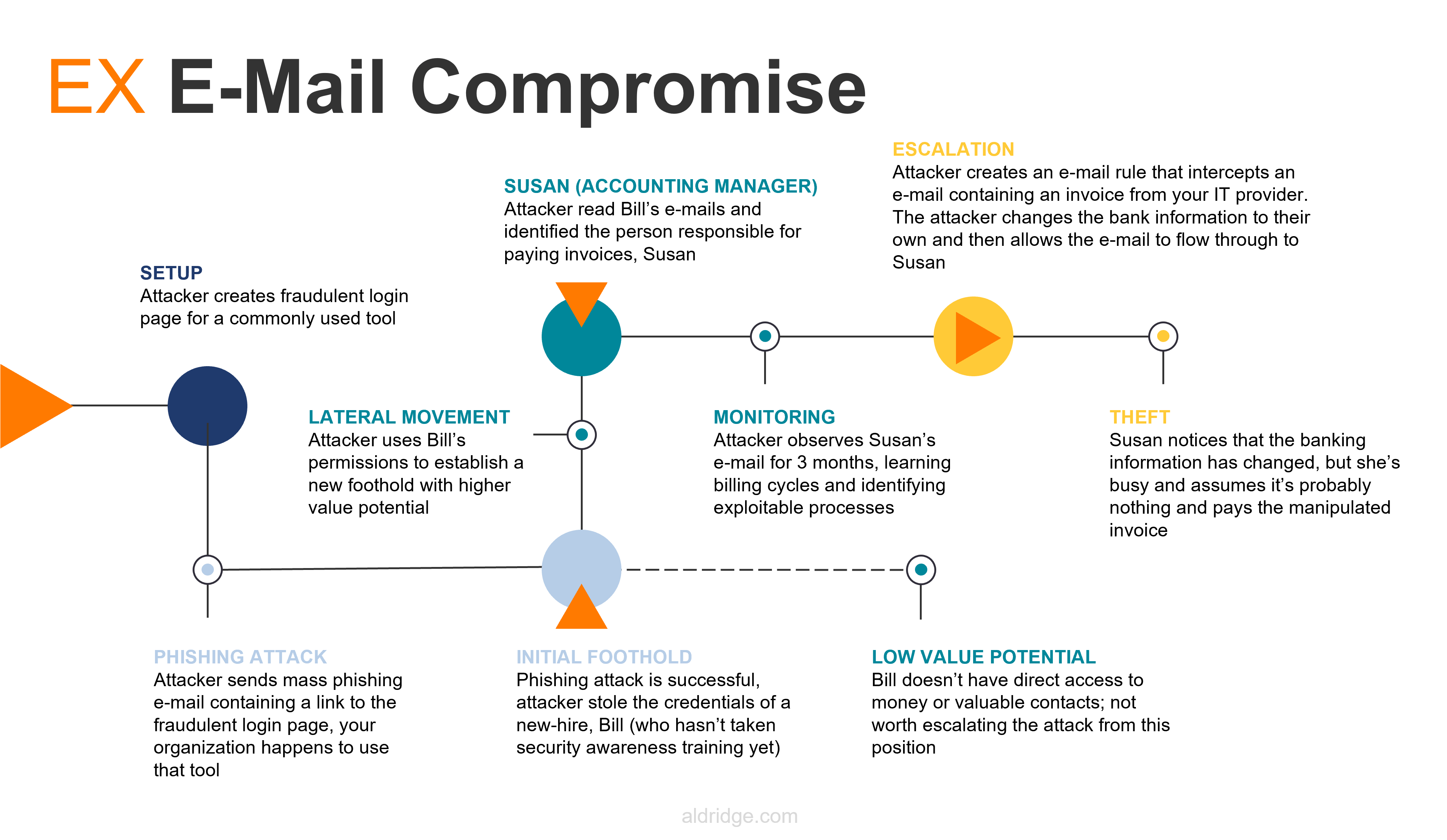
A bad actor sets out with the goal of finding someone with financial responsibility or IT administrative access to trick them into sharing their credentials with the attacker or installing malicious software inside their network.
If the cybercriminal starts out with a shotgun-style approach, they have no specific target in mind. They will conduct a low-effort attack on a large number of businesses. They may set up a fake website that accepts usernames, collects passwords, and possibly mimics a common internet service. Then, they will launch a marketing campaign to try and entice users to visit that site and provide their credentials. You may even receive an email about your account expiring from a well-known service.
The bad actor is trying to get you to click on their fraudulent link and trick you into giving them your corporate email credentials. Even if the attacker has an extremely small success rate, the massive number of targets means that there will be plenty of people that fall for the scam.
How A Business Email Compromise Happens
Bill, our hypothetical employee, is one of the recipients of the phishing email. He hasn’t taken security training, and he doesn’t have multi-factor authentication enabled. Bill thinks that the fraudulent email he received is legitimate, so he clicks on the link and attempts to log into the fake login page. The site then displays an error or something else that raises concern for Bill, but he decides to ignore it and goes on about his day.
The bad actor can now log into your systems with Bill’s credentials to see who Bill is and what he does. Now they are in your IT systems, reading Bill’s emails, looking at his documents, and testing what Bill can access. Luckily, the bad actor determines Bill doesn’t have any significant purchasing or financial authority. It’s a dead end.
Or is it?
While going through Bill’s emails and chats, the bad actor discovers Susan has the financial authority they need. The bad actor can see from Susan’s signature that she’s the accounting manager. Acting as Bill, the bad actor sends Susan an email from inside the organization to try and trick Susan into providing her credentials.
Successfully exploiting Susan’s trust, the bad actor now has access to Susan’s account. By monitoring what she does, what her normal activity is, and who she regularly corresponds with, the bad actor learns Susan’s work patterns. They can now select an exploitable target and make their attack.
The attacker knows an invoice from a vendor arrives on the 1st of every month with a predictable subject line. They create an email rule that will intercept the invoice email (based on its subject line) and deliver it to a hidden folder Susan doesn’t know about. The bad actor replaces the payment information on the invoice with their own and lets the email flow through to Susan’s inbox. Susan sees the invoice, notices the payment information is different, but doesn’t think much of it and pays it.
A week later the vendor reaches out to Susan to remind her about her unpaid invoice. After some back-and-forth, Susan and the vendor realize what has happened but it is already too late. Money that is wired overseas is rarely able to be recovered.
How Can Cybersecurity Stop A Business Email Compromise?
If the attack chain was broken at any point along the way, the entire attack would have failed. A comprehensive IT security solution could have broken the business compromise attack chain at these points:
- Phishing Email: If the target organization had anti-spam email policies in place or utilized an email security tool like Microsoft Defender for Office 365, it is possible no one from the target company would have received the email in the first place.
- Stealing Bill’s Credentials: Bill should have been assigned security awareness training when he started his job. If he had gone through training, he would have been able to recognize the phishing attack and likely not have fallen for it. If he still fell for it (because these things happen), he would have known to immediately report it to his IT team so they can secure his account before any damage occurs.
- Accessing Bill’s Account: If the organization had proper access management, someone logging into Bill’s account would have to enter a Multi-Factor Authentication token that only Bill would have access to, preventing the attacker from getting inside.
- Manipulated Invoice: It is a security best practice to call your vendors/partners to confirm a change in payment information before transferring money. If the victim organization had a policy in place, Susan would have double-checked with the vendor and caught the attack before the money was wired.
A well-thought-out security strategy can make it more difficult for a cyberattack to succeed. Although you can never be 100% secure, you can drastically mitigate your risk by implementing a solid baseline level of security technology, supported by a company culture that recognizes the importance of security and adheres to your policies and procedures.
Hear our CIO, Chad Hiatt, talk about this topic from a recent webinar.






