The terms “security events,” “indicators,” “incidents,” and “breaches” are often thrown around in discussions about cybersecurity. But what exactly do they mean for your organization? At their core, these terms revolve around one central question: Has one of your assets been compromised?
How Are Assets “Compromised”? 3 Key Violations
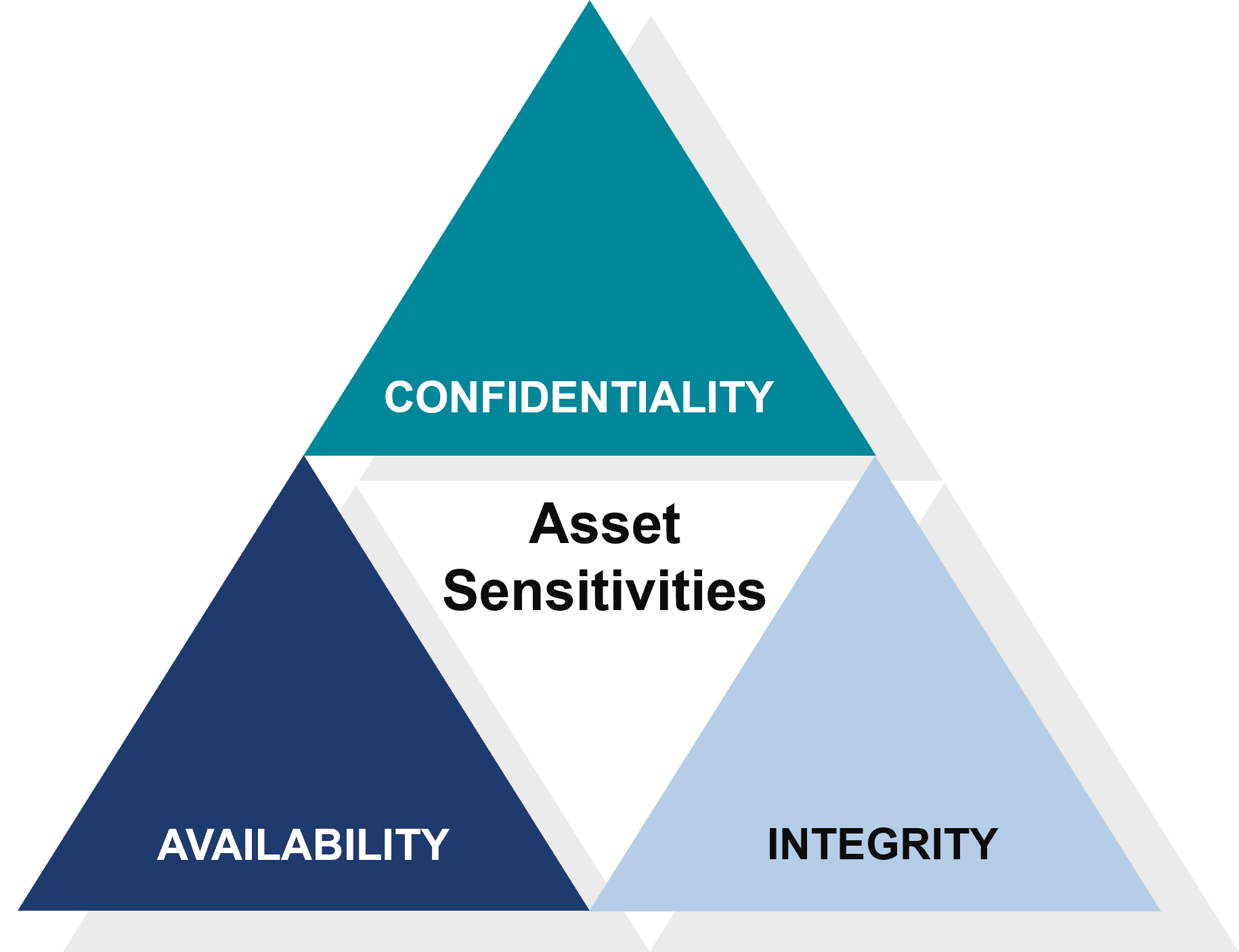
Asset Compromise: The Three Key Violations
When we talk about an asset being compromised, we’re talking about compromises to that asset’s confidentiality, integrity, or availability.
Confidentiality Breach:
- This occurs when a threat actor gains unauthorized access to an asset and can read or extract private information.
- Sensitive data, such as customer records or proprietary business plans, fall into the wrong hands. The consequences can be disastrous, leading to breaches of privacy regulations, loss of trust, and financial repercussions.
Integrity Compromise:
- Integrity compromise involves the manipulation of an asset by a threat actor, rendering it unusable or unreliable.
- Critical files or databases are tampered with, leading to incorrect information, system malfunctions, or even data corruption. The impact on business operations and decision-making can be severe.
Availability Disruption:
- When a threat actor compromises the availability of an asset, they prevent authorized users from accessing it.
- Essential systems or services are unavailable due to a cyberattack or malicious activity. This disruption can disrupt operations, cause downtime, and result in significant financial losses.
Understanding the Threat Actor’s Strategy
Why do threat actors target assets and aim to compromise their confidentiality, integrity, or availability? Their motives vary, but typically they seek to:
- Extract money through ransom demands or extortion schemes.
- Inflict harm or damage to your organization’s reputation.
- Use compromised assets as a foothold to launch further attacks or infiltrate deeper into your network.
Protecting Your Valuable Assets
As you assess what holds value within your organization, it’s essential to consider the potential impact of a confidentiality, integrity, or availability breach on each asset. Here are some key steps to protect your assets:
- Identify Critical Assets: Determine which assets are most valuable and prioritize their protection based on their importance to your business operations and objectives.
- Implement Layers of Protection: Deploy robust cybersecurity measures, including firewalls, encryption, access controls, and intrusion detection systems, to safeguard your assets from unauthorized access, manipulation, or disruption.
- Regular Monitoring and Response: Establish proactive monitoring mechanisms to detect security events and indicators of compromise early. Develop incident response plans to contain and mitigate breaches swiftly, minimizing their impact on your organization.
- Educate and Empower Your Team: Provide cybersecurity awareness training to your employees to help them recognize and respond to potential threats effectively. Encourage a culture of security consciousness and accountability across your organization.
Safeguarding your organization’s assets from cyber threats is paramount. By understanding the nuances of security events and taking proactive steps to protect your assets’ confidentiality, integrity, and availability, you can mitigate risks, strengthen resilience, and safeguard your organization’s reputation and success.
Watch the Full Webinar
Experts from Buchanan, Higginbotham, and Aldridge give an update on today’s cyber threats, and why it is only a matter of time before your business will be breached. If you start planning for an attack today – thinking through your risks and implementing the right risk management tools, you can survive any cyberattack. Watch the full Prepare, Respond, & Recover webinar to see how you can start planning.






