Having a well-structured incident response plan (IRP) is essential for effectively managing security incidents. One crucial aspect of this plan is the integration of an incident response team to supplement and enhance your internal capabilities.
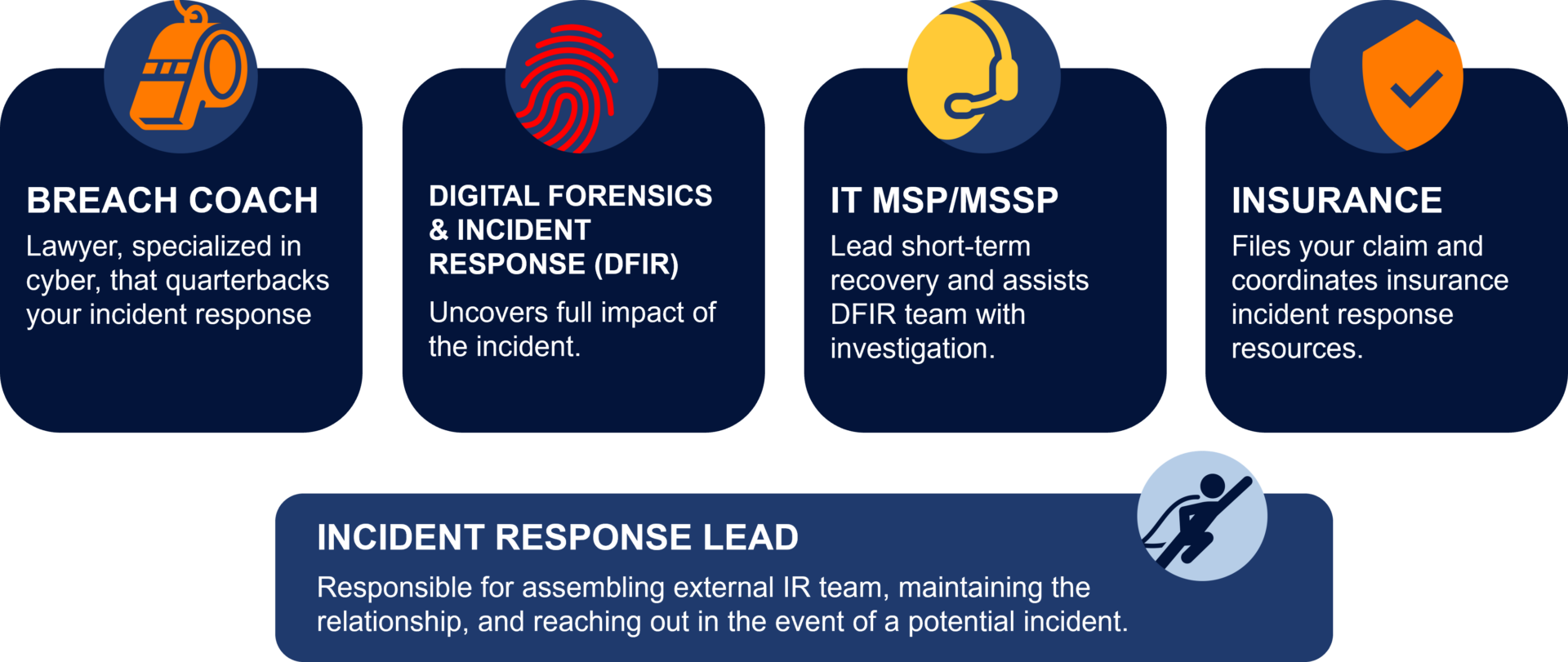
External Incident Response Team Roles & Responsibilities
External incident response teams bring specialized expertise and additional resources to your organization. It’s essential to identify these external players early in your planning process. Engaging them in training scenarios, such as tabletop exercises, ensures that everyone involved practices together, fostering seamless collaboration during a real incident. Your external IR team should consist of:
- Breach Coach: A lawyer who specializes in cybersecurity that quarterbacks your incident response
- Digitals Forensics & Incident Response (DFIR): Uncovers the full impact of the incident
- IT MSP/MSSP: Leads short-terms recovery and assists the DFIR team with the investigation
- Insurance: Fles your claim and coordinates insurance incident response resources
Building Your Internal Incident Response Team
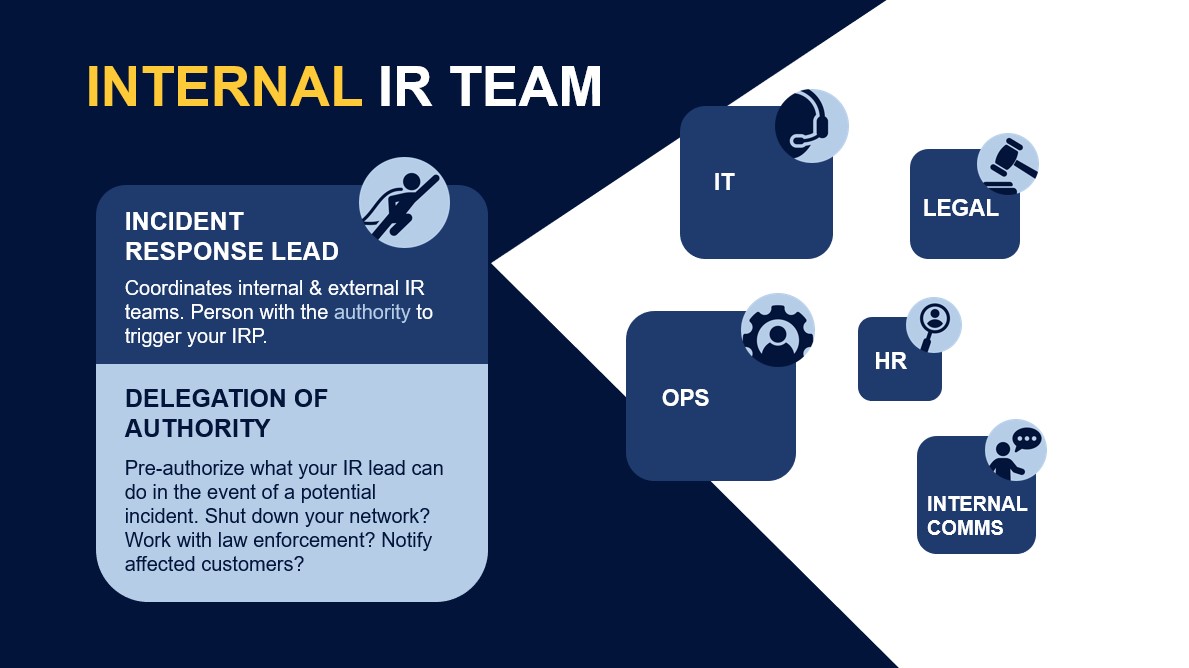
Your internal incident response team typically consists of members from various departments, including:
- Information Technology (IT): Responsible for technical response and system recovery.
- Legal: Ensures compliance with laws and regulations while managing legal risks.
- Human Resources (HR): Assesses potential data breaches related to employee information.
- Internal Communications: Crafts internal messages to keep employees informed.
- External Communications/Marketing: Manages external messaging to protect the organization’s reputation.
- Operations: Evaluates the incident’s business impact.
Each department plays a vital role in addressing different facets of an incident, ensuring a comprehensive response.
Delegation of Authority
A well-crafted incident response plan must include a delegation of authority. Incidents often occur outside standard business hours, making it crucial to have designated leaders who can make swift decisions. Typically, this authority is granted to the Chief Information Officer (CIO) or the Chief Information Security Officer (CISO).
In scenarios where immediate action is required—such as disconnecting the network to prevent further damage—these leaders must act without waiting to consult the CEO. Establishing trust and authority in advance streamlines decision-making during crises.
Identifying the Incident Response Lead
A key figure in the incident response process is the Incident Response Lead. This individual coordinates all activities and communications across various teams. While the lead may come from IT or legal, it’s best if they are not directly managing technical responses to avoid conflicts of interest. The Incident Response Lead should be a senior member capable of making decisions that affect the organization’s response strategy.
By ensuring that all teams—internal and external—are well-prepared and coordinated, you can respond effectively and minimize the impact of security incidents. Establishing clear roles, delegating authority, and identifying a strong Incident Response Lead will set your organization up for success in navigating the complexities of cyber threats.
Create Your First Real Security Incident Response Plan
Watch the full webinar to learn how to make a real security incident response plan in just 1 hour. No, we’re not talking about a pretend plan that only serves as a CYA for insurance – we’re talking about a step-by-step plan that you can rely on in a crisis.







