You may have heard about Log4j earlier this year. It was a big enough deal that it received coverage on mainstream news sites.
Log4j refers to a common software utility that’s commonly found on many web services. Its intended use is for logging the health and activity of those web services for administrators, providing insights into the services’ health, performance, and utilization. Log4j is not just used for Internet-facing, public web services, many server applications, and service companies use Log4j inside their own networks to leverage its diagnostic logging capabilities.
The Log4j Vulnerability
The Log4j vulnerability was a zero-day exploit, meaning the bad guys knew about it before the good guys did and before manufacturers could fix the vulnerability. More than that, Log4j is so widely used that almost every business had some sort of exposure to the vulnerability.
If the vulnerable device is connected directly to the internet, a bad actor can technically attack that Log4j-vulnerable device from anywhere in the world. The attack starts with the bad actor using readily available tools to scan the internet for businesses that are actively using known vulnerable devices. The attacker will select a target and manipulate the vulnerable device into running malicious code. The device could be something seemingly harmless like a printer or a camera, but because that device is connected to your network, it can be used as a stepping stone to compromise higher-value systems. Read a more in-depth explanation of the Log4j Vulnerability.
Example of a Log4j attack
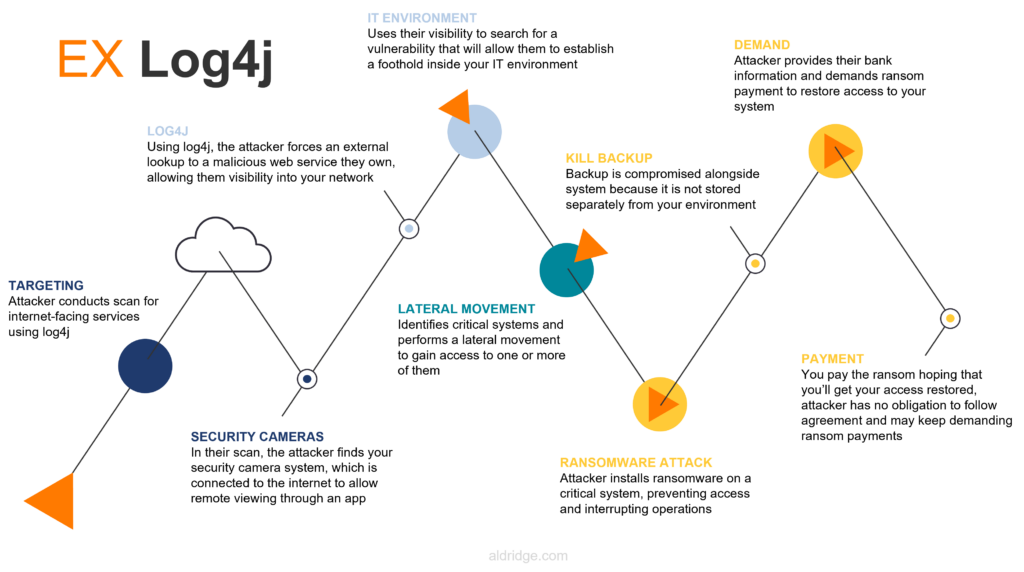
A cyber criminal conducts a scan for businesses that use web-enabled video cameras that also utilize Log4j. They identify a company that uses security cameras that connect to the internet because the owner likes to be able to check the camera feed using an app on their phone.
The attacker exploits the Log4j vulnerability in the security cameras to gain visibility into the organization’s network. From there they perform a lateral movement to get inside a business-critical system. The attacker installs ransomware on this system, causing a company-wide disruption. The target business did not properly segregate their backups from their network, so the attacker was able to shut those down too.
The attacker demands a ransom payment to restore access to the systems they locked down. Unfortunately, criminals have no obligation to honor the agreement if a ransom payment is made. If the company identifies itself as someone willing to pay, the bad actor may continue demanding further payments.
How to Protect against a Log4j exploit
Protecting against this type of zero-day attack can be achieved by
- Managing your IT surface area by working with your IT team to understand all the devices you’re running and making sure they are up-to-date and supported
- Getting cognizant and selective about what’s visible from the internet by regularly performing external vulnerability scans
- Putting internal sensors and eyes in place to detect unusual traffic, even if it’s happening from inside your office–we expect to see cases of criminals who sat inside networks undetected for years, waiting for a good time to attack.
Security tools are needed to break those chains and defend against motivated, current-generation threats and bad actors. In addition to fundamental security tools, education, and best practices, a good security team is needed to monitor the environment, put the pieces together, and respond to suspicious activity.
Hear our CIO, Chad Hiatt, talk about this topic from a recent webinar.







