Microsoft 365 Business Premium is our recommended Microsoft 365 subscription plan for any professional organization. The value you receive for just $10 per user/per month over Business Standard is too good to pass up, especially for businesses that value security. Here are 3 of the main benefits your business will receive from a Microsoft 365 Premium plan
3 Benefits of Microsoft 365 Business Premium
1. Email Security Through Microsoft Defender For Office 365
Phishing attacks, or fraudulent messages that aim to steal money or privileged data, are the most common cyber attack targeting businesses. Microsoft Defender For Office 365 will provide you with the tools necessary to protect your inbox and fend off the vast majority of email-based attacks, including:
- Safe Attachments – Automated investigation of all email attachments opens them in a safe virtual environment (i.e. detonation) to detect, by their behavior when launched, if they contain malicious software that could cause damage.
- Safe Links – Scans all links to determine if they go to any known malware sources, will re-test the link every time it is clicked on to make sure that the destination hasn’t been changed to a malicious site.
- VIP Impersonation Protection – Apply a higher standard of scrutiny to e-mail originating from outside the client’s organization from senders with names matching or substantially similar to defined key people within their organization. Warns users in their Microsoft Outlook e-mail client if the message appears to be impersonating an individual within their organization but actually arrived from a source outside of your organization. Assists your users in identifying potential phishing attacks before they cause harm to your organization.
- Zero-Hour Auto Purge (ZAP) – If an email is reported as malicious or spam, ZAP will find and quarantine that email from other user’s inboxes across your organization.
- Quarantine – Your IT administrator can set up quarantine policies that will prevent high-risk emails from reaching your teams’ inboxes. Instead, these risky emails will be quarantined so that your IT team can investigate these emails and take further action if needed.
2. PC & Mobile Device Management
Your security policies are only effective if they are applied to every device that can access your data. With the rise of remote work, employees are using their personal devices for work more than ever before. This has posed a significant security challenge because personal devices are rarely under IT management and lack the security controls that corporate-managed devices have. Microsoft Business Premium addresses this problem through Intune. Intune will allow you to:
- Deploy Office apps, security policies, and updates to all company-managed devices.
- Protect your data on your employee’s personal devices without violating their privacy and trust. Intune enforces compliance policies only on apps that contain company data (like Office apps). Whenever someone tries to access company data on their personal device, Intune will check that their device meets certain security standards (e.g. password protected) and verify that they have permissions to that data before granting access.
- Connect devices to Microsoft Defender for Endpoint, allowing you to block devices that fail security checks or that exhibit other unusual behaviors.
- Remotely wipe company data from lost or stolen devices.
3. Identity & Access Management
Your IT team needs the ability to manage your employee’s user profiles and their permissions to maintain the integrity of your network and your data. Microsoft 365 Business Premium comes with Azure Active Directory P1, a cloud-based Identity & Access Management solution. Azure AD offers:
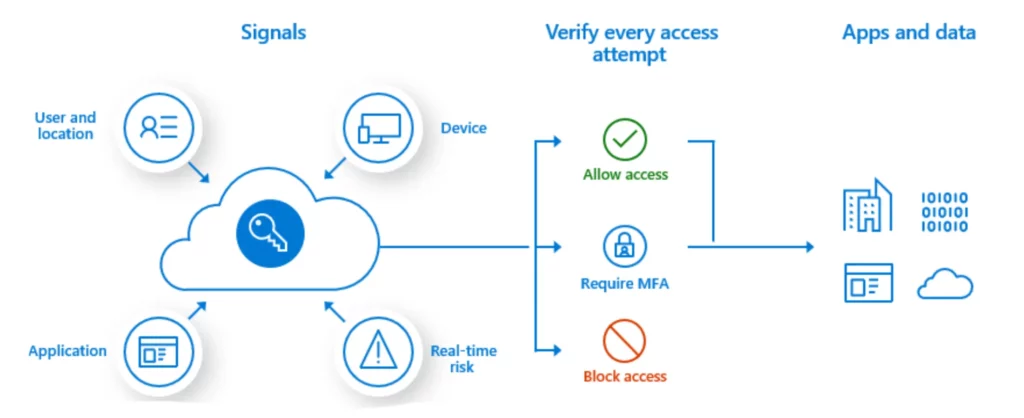
- User Account Management – A database of your organization’s users, their information, devices, and permissions. Enables your IT team to securely connect your employees with the network resources they need to do their job. A well-managed Active Directory is necessary to enable conditional access, or the protection of privileged information by requiring that certain criteria be met before someone can access that data. Here is how conditional access works:

- Conditional Multi-Factor Authentication (MFA) – Challenge users on log-in to prove they are who they say they are by entering a code that is sent to their phone or some other token that only they would have. Conditional MFA means that you have far greater control over how MFA is utilized. For example, you can only challenge people with an MFA prompt if suspicious activity is detected (i.e. signing in from a new location or an unknown device), or require that someone authenticates themselves every time they access certain high-value information.
- User Security Groups – Organize your people by their job function, risk factors (e.g. remote employee), or any other relevant attribute into security groups. You can control the group’s permissions and security policies so that your team only can access the tools and data they need to do their jobs. High risk groups can be more tightly controlled without applying those same policies across your organization.
- Single-Sign On (SSO) – Allows you to securely sign into a different tools using a single set of login credentials.
Upgrade to Microsoft 365 Business Premium
If you are considering implementing Microsoft 365 Business Premium in your business, there are a few things to keep in mind:
- Most of the tools included in Premium are not going to provide their full potential value right out of the box. They must be configured to properly function in your IT environment and utilize custom IT and security policies that support the specific way you and your team works with your data.
- You need to periodically evaluate the effectiveness of your Microsoft 365 solution so that you can make sure everything is working as intended and optimize the individual tools as needed.
- You do not have to do it alone. As a Microsoft 365 Gold Partner we provide turnkey Microsoft 365 implementations and management to small and midsized organizations. If you’re interested in an Aldridge Microsoft 365 implementation, please fill out the form at the bottom of our IT Projects page. We will answer any of your Microsoft questions, help you determine if we’re the right partner, and help get you started on your implementation.