Who We Are
Aldridge is an IT and security managed services firm, based in Houston, Texas. Founded in 1984, Aldridge has been helping businesses get more value from technology for 40 years. Although much has changed in IT over the years, our core mission has always been the same – to maximize the impact of technology on people so that they can work smarter and accomplish more.
We are passionate problem solvers that are always looking for new ways to use technology to bring value to the businesses we support. Partner with Aldridge to start using technology to empower your business, and gain peace of mind that whenever you need help, we will be right there with you.
We work with:
- Business owners and executives that just want IT to work – they want to focus running their business and not on their technology and security.
- Operations and business managers who want less downtime, reliable service, and better security.
- CIOs, CTOs, and IT Managers who want to get out of day-to-day IT and focus on strategic initiatives.
What We Do
IT Managed Services
IT Consulting
IT Managed Services
Does your IT need a little or a lot of help? We can help your current IT team by filling in the gaps, or take care of IT completely. Partnering with Aldridge will allow you to focus your core competencies and strategic goals, while leaving IT in the hands of Aldridge experts.
How We Think about IT – Our Framework for Successful IT
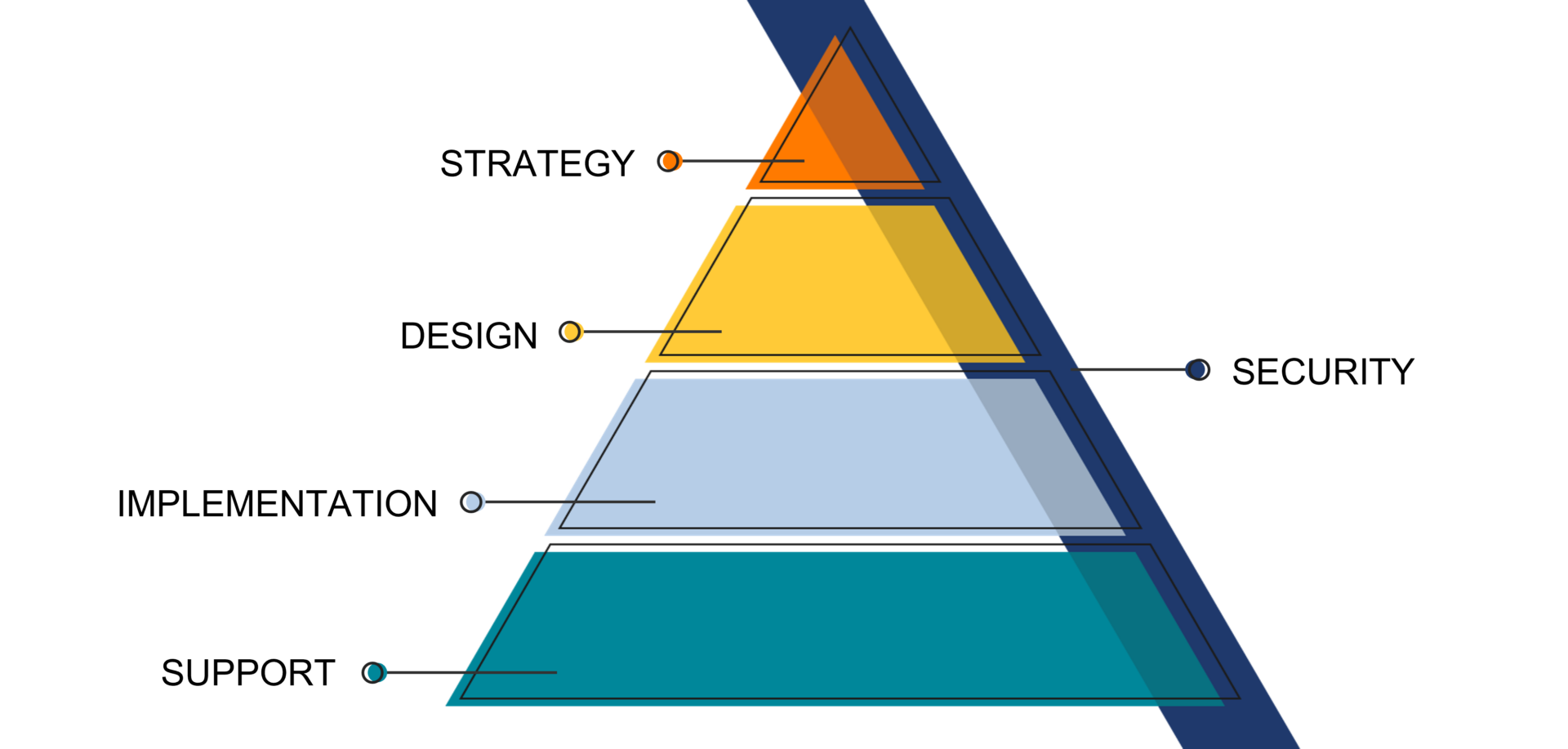

Strategy
We’ll work with you to create an IT strategy that supports your business goals and adapts to changes in technology and cybersecurity threats.
18-24 Month IT Roadmap & Budget | Policies & Procedures
Design
Our solutions architects will design technology solutions that fit your business needs and budget.
Solution Research & Development | Technology Catalog

Implementation
We’ll create and maintain a strategic IT roadmap and budget for your business, outlining major initiatives for the next 18-24 months to reduce surprise costs and downtime.
IT Projects | End-to-end Procurement Process

SUPPORT
We’ll provide a dedicated, local IT support team that knows you, your team, and your business to ensure productivity and efficiency.
95% CSAT (last 90 days) | 9 Seconds (median phone ring time) | 97 minutes (median time to resolve critical issues)
Security
We developed IT Security Levels to help businesses prioritize their security technology implementations, protecting their network, endpoints, cloud, internet access, and applications.
Managed Detection & Response | Security Incident Management | Backup & Recovery

Cybersecurity
Defending your company from today’s cyber threats requires modern IT security tools, a security-minded culture, and policies based on a well-defined security posture. Read below to learn about the key components of an IT security strategy, and receive our most current guidance and best practices.

Identify
Develop a risk management plan that fits your budget and risk tolerance by assessing your organization’s threat profile.

PROTECT
Secure devices, critical systems, and data by using security tools and industry-standard policies/procedures.

DETECT
Security & NOC teams monitor devices and networks 24/7, and EDR on managed devices stops malicious activity.
RESPOND
Security team validates alerts, investigates damage scope, and engages NOC team to begin recovery process.

RECOVER
Recover business-critical systems and assist with long-term recovery through the cyber insurance claims process.
Advanced Security Solution: SECURITY +
Do you require a comprehensive security strategy supported by cutting-edge tools? Are you in a regulated industry that has strict compliance obligations, or do you work with highly valuable data that needs more robust protection? If you are serious about your cybersecurity, you need Security+.
Security + Includes:
Security Incident & Event Monitoring (SIEM)
Security Operations Center (SOC)
Cyber Attack Recovery
External Vulnerability Management
Identify your internet-facing services vulnerabilities, talk through risks, and guide remediation efforts.
Security Awareness Training & Mock Phishing Attacks
Educate your team on proper security hygiene and conduct routine mock attacks to raise your team’s vigilance and identify who needs supplemental training.
Dark Web Monitoring
Scan the marketplaces where stolen information is traded for your domain, and provide a report showing all at-risk credentials.
Web Filtering
Block known malware sources and prevent access to business-inappropriate sites.
Behavior-Based Multi-Factor Authentication (MFA)
Add MFA to your Windows servers & add conditional access to your Microsoft 365 MFA.
Deep Email Filtering
Protect your teams’ inboxes through advanced email filtering, VIP impersonation protection, and scan links and attachment for malicious activity.
IT Consulting

Big-Picture Planning
Adhere to a consistent vision when making big-picture IT decisions. The
decision process is centered around the business requirements, Total Cost of Ownership (TCO)
of the effort, and the Return on Investment (ROI) of the IT solution.

Identify Problems for Resolution
Collaborate with your leadership team to uncover issues
facing your organization that you may not have known were there and to outline how technology
can help solve the major problems facing your business.

Time Management
Avoid implementing an IT solution that will inevitably break in the future,
causing you to experience the same IT issue again and again without a concrete resolution.

Proactive Communication
Clearly communicate IT trends, risks, knowledge, and opportunities
to your business executives by holding IT update and planning meetings with your leadership
team to prepare for your organization’s future IT needs.

Playing Devil’s Advocate
Question the intention of the IT solution. Systems must talk to one
another to work together properly, and it’s the CIO’s responsibility to help you make IT decisions
that will support your business needs now and in the future.
Ready to get IT that just works?
Fill out this form, and we’ll be in touch.






