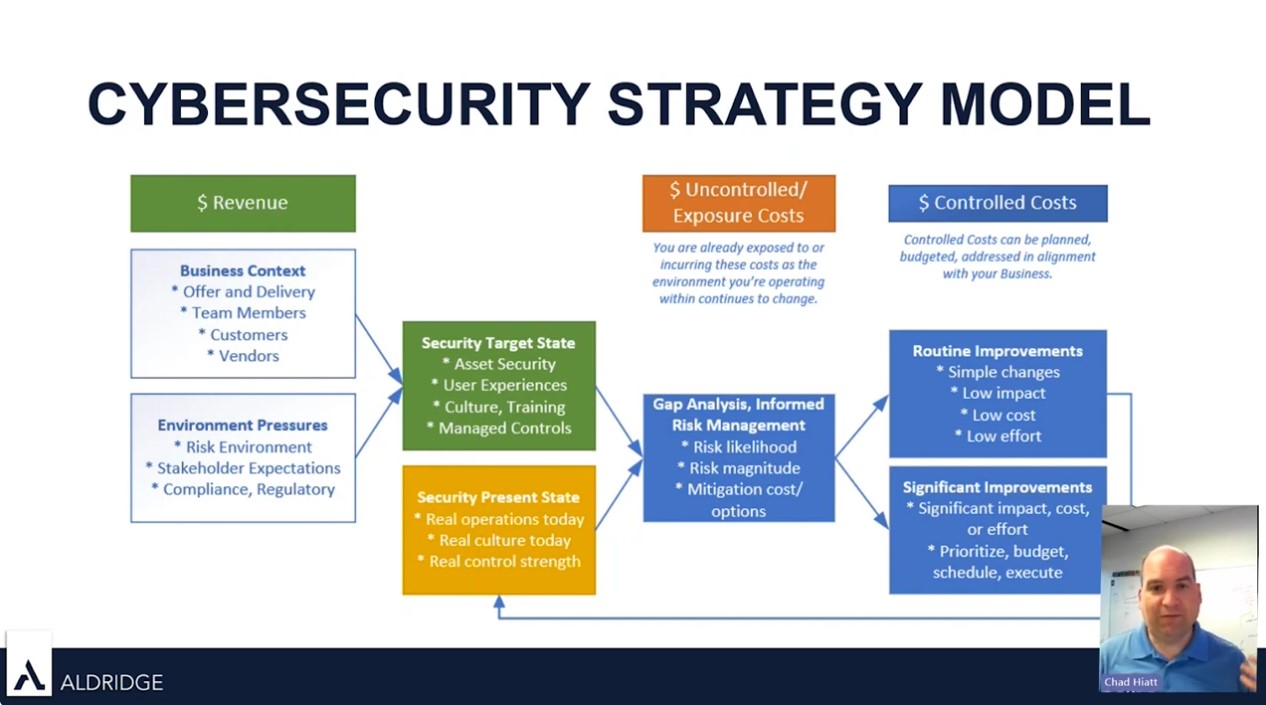
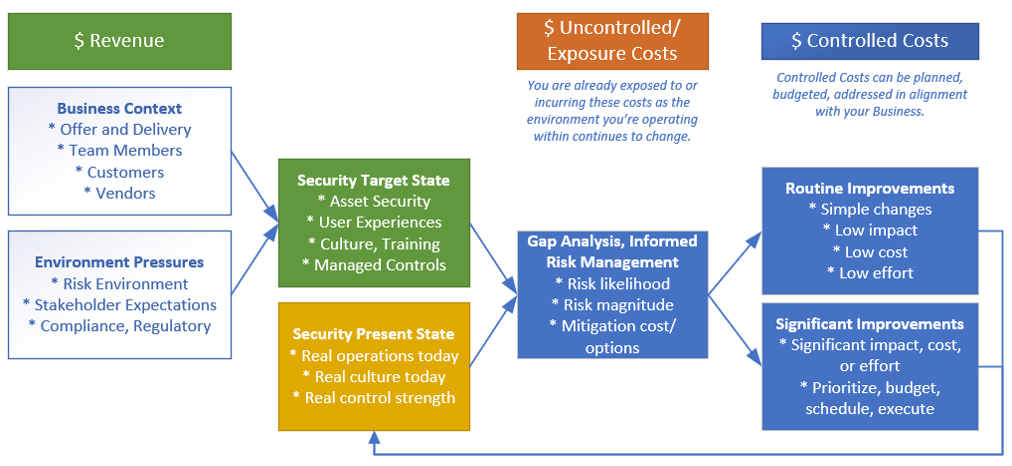
Developing a strong cybersecurity strategy requires that you know where you are today, where you want to be, and how to bridge that gap.
Our Cybersecurity Strategy Model for Executives
The Cybersecurity Strategy Model
One effective approach to developing a cybersecurity strategy is to visualize the journey from your present state to your target state.
Defining Your Target State
The first step in this model is to define your target state—the ideal level of security your business aims to achieve. This target state should be tailored to the unique aspects of your business operations and the specific environment in which you operate. Factors to consider are:
- Industry regulations
- The nature of your data
- Risks unique to your business
Assessing Your Present State
Next, assess your present state—the current level of security within your organization. Conduct a thorough evaluation of your existing security measures, identifying strengths and pinpointing vulnerabilities.
Comparing your present state with your target state reveals the gaps that need to be addressed.
Identifying & Prioritizing Improvements
Once you have a clear understanding of the gaps, create a list of potential improvements. These can range from routine updates with low risk to significant changes that might require substantial investment and careful risk management.
Prioritize these improvements based on their impact on your overall security posture and the resources required for implementation.
Implementation
Implement the prioritized improvements thoroughly. As each improvement is made, it feeds back into your present state, enhancing your overall security. This ongoing process allows for continuous reassessment and adjustment, ensuring that your security measures evolve in response to new threats and changing business needs.
WATCH THE FULL VIDEO
Aldridge’s CTO, Chad Hiatt, talks on cybersecurity updates and the ‘Right of Boom’ concept. Watch the full video to see how you should be thinking about security, gain valuable perspectives on the evolving LOTL threat landscape, learn about the new best security practices of 2024, and using a cybersecurity strategy model for success.