The short story on cybercrime is that it is getting worse – it is not a matter of if, but when your business will get breached. The good news is that you have control over what happens to your business when you get attacked. If you take security seriously and plan for an attack before it happens, you can minimize the disruption and damage to your business.
Quick Navigate
- 2024 Core Security Controls
- The Attack Chain
- Disrupting The Attack Chain with Core Security Controls
- Key Takeaways
Cyber Threat Update
Phishing is still king, ransomware is dropping
Social engineering attacks, phishing and tech support scams continue to be the top cyberattack tactic. People are much easier to compromise than your IT. It is critical that you provide security awareness training to your team and build a security-minded culture.
Extortion, or ransomware attacks, are losing favor. We expect this is because businesses have learned how to properly back up their critical systems and data. If you have an air-gapped backup, meaning the backup is not stored on your network, you can simply restore your systems if they get locked down by an attacker.
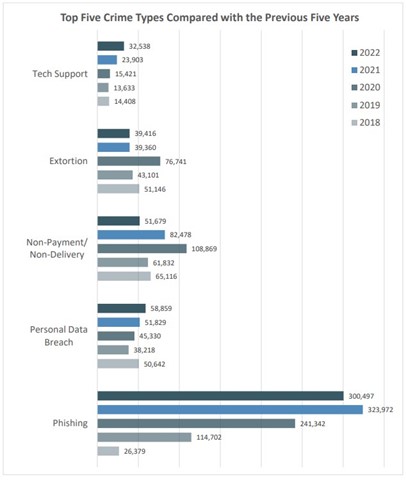
Source: ic3 Complaint Statistics
Losses are rising
Losses from cybercrime continue to rise year after year, 2022 saw about a 50% increase in losses from the year prior. Keep in mind, these figures are only from incidents reported to law enforcement – the true loss figure is significantly higher. This report, even if it does not include every case, shows the trend that losses are rising.
It is important that you report any case of cybercrime to law enforcement through IC3. Even if you do not need law enforcement’s help, you are giving them visibility into your case and the information they get from you could let them help someone else if they are targeted by the same threat actor.
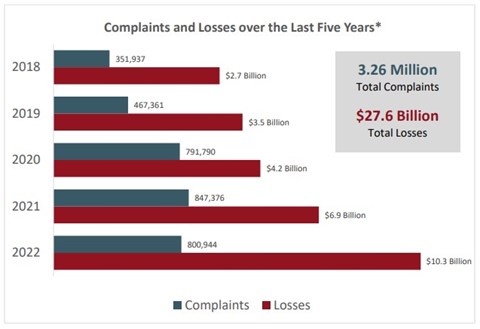
Source: ic3 Complaint Statistics
Top Industries Effected by Ransomware
Although ransomware is losing popularity, that is not necessarily the case for attackers targeting certain industries. Healthcare, manufacturing, and government remain vulnerable to ransomware attacks. These industries usually have large, complex, and outdated IT and they will pay anything to get access back to their data and systems.
If you pay a ransom, you run the risk of being fined by the government. Ransomware funds hostile nation-states and terrorist organizations. Do not put yourself in the position where you must pay a ransom to keep your business running, it is a lose-lose situation.
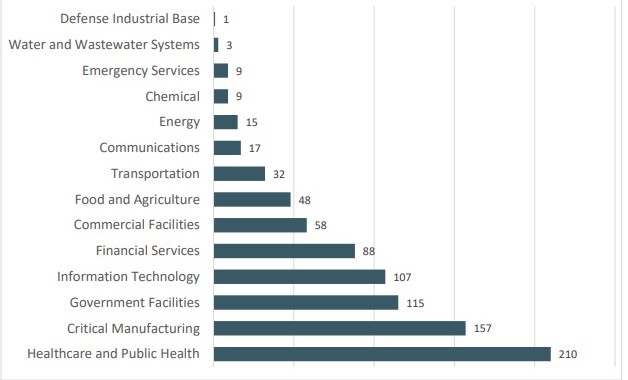
Source: ic3 Internet Crime Report
The FBI can help you recover stolen assets
If someone on your team wires money to a threat actor, report it to ic3.gov as soon as possible. Be prepared with any financial information you can provide. If you report the fraud within 24 hours, the FBI has about an 80% success rate in recovering fraudulently wired funds.
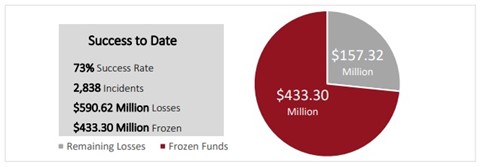
Source: ic3 Internet Crime Report
2024 Core Security Controls
You must grow your security program as threats evolve. Your security program consists of 2 types of security controls, technical and organizational. Below is the full list of security controls we consider core to any well-prepared business’s security program.
Technical Controls:
Technical controls include your choices as to what makes up your IT environment and tools, as well as your choices in how those elements are configured and used. Technical also includes the security tools put around them and integrated within them to identify, protect, and detect unusual activity.
- Secured Data Backup
- E-mail, Teams Security Filtering
- Managed Detection & Response (MDR)
- Conditional Multi-Factor Authentication (MFA)
- External Vulnerability Scanning
- Internet Site Access Filtering
- Dark Web Monitoring
- Security Information & Event Management (SIEM)
Organizational Controls:
Organizational controls include you regularly driving the importance of a security mindset within your organization culture and being good keepers of your customer and partner trust.
- Current IT Asset Inventory
- IT Risk Consideration & Design
- Recovery Readiness Planning
- Security Awareness Training
- Simulated Phishing Testing
- Cyber Security Insurance
- Incident Response & Recovery Plan
- Bring Your Own Device (BYOD) Policy
- 24/7 Security Operations Center (SOC)
You have a large list of security controls, but how do they protect your business? Great question, let us step through the attack chain so you can understand how cyberattacks work and how these controls disrupt the attack chain.
The Attack Chain
An attack is typically not one single event, it is also not just one specific series of events, but the actions and events tend to fall into four phases.
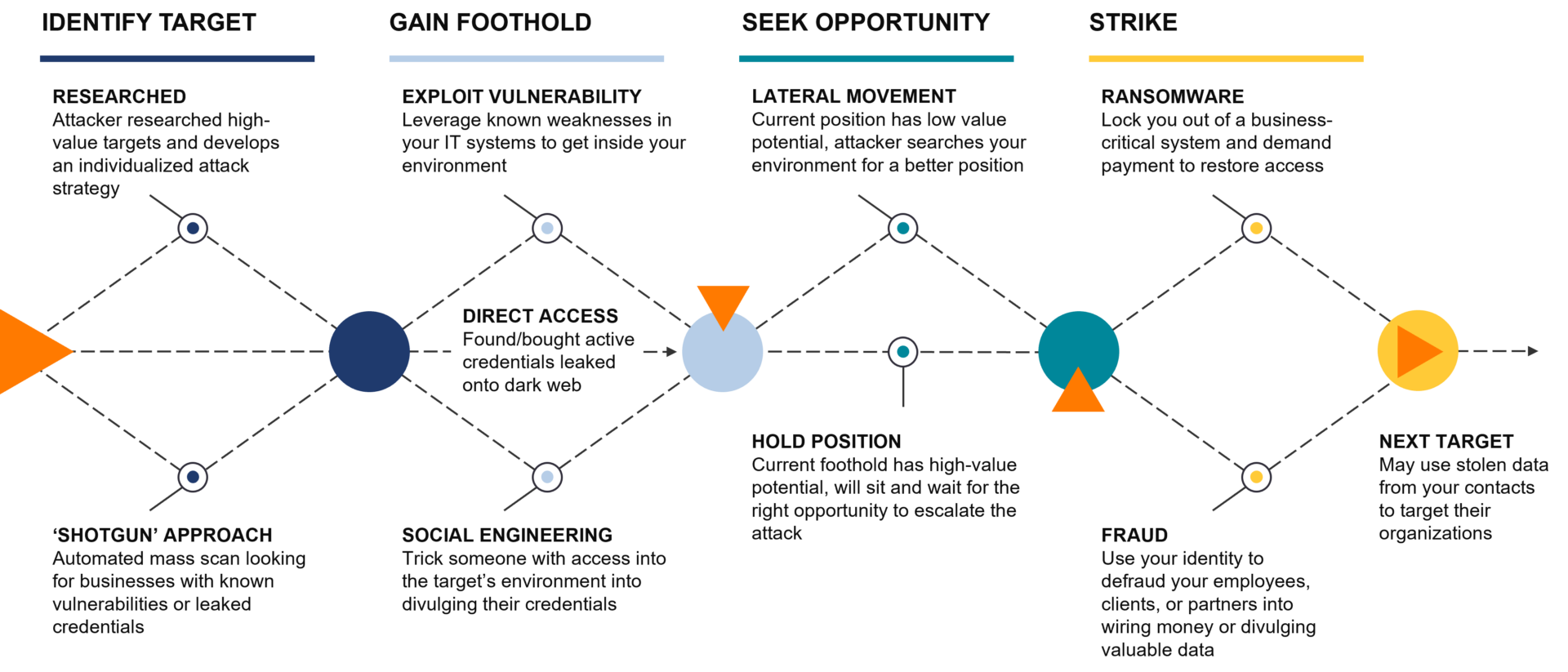
Identify Target
The attack chain starts out with the threat actor identifying a candidate target. They may have become aware of your organization from compromising one of your contacts or vendors. Or some aspect of your business – your industry, the technology you have, etc. – put you on one of their target lists.
Gain Foothold
Once they have identified a potential target – your organization – they then try to gain a foothold in your IT infrastructure. They might try to compromise an individual user’s account via phishing or another form of fraud, or they might try to leverage a weakness in your IT environment’s configuration. The threat actor can bypass all of that and buy access directly into your environment if you have had active credentials into your IT leaked on the dark web.
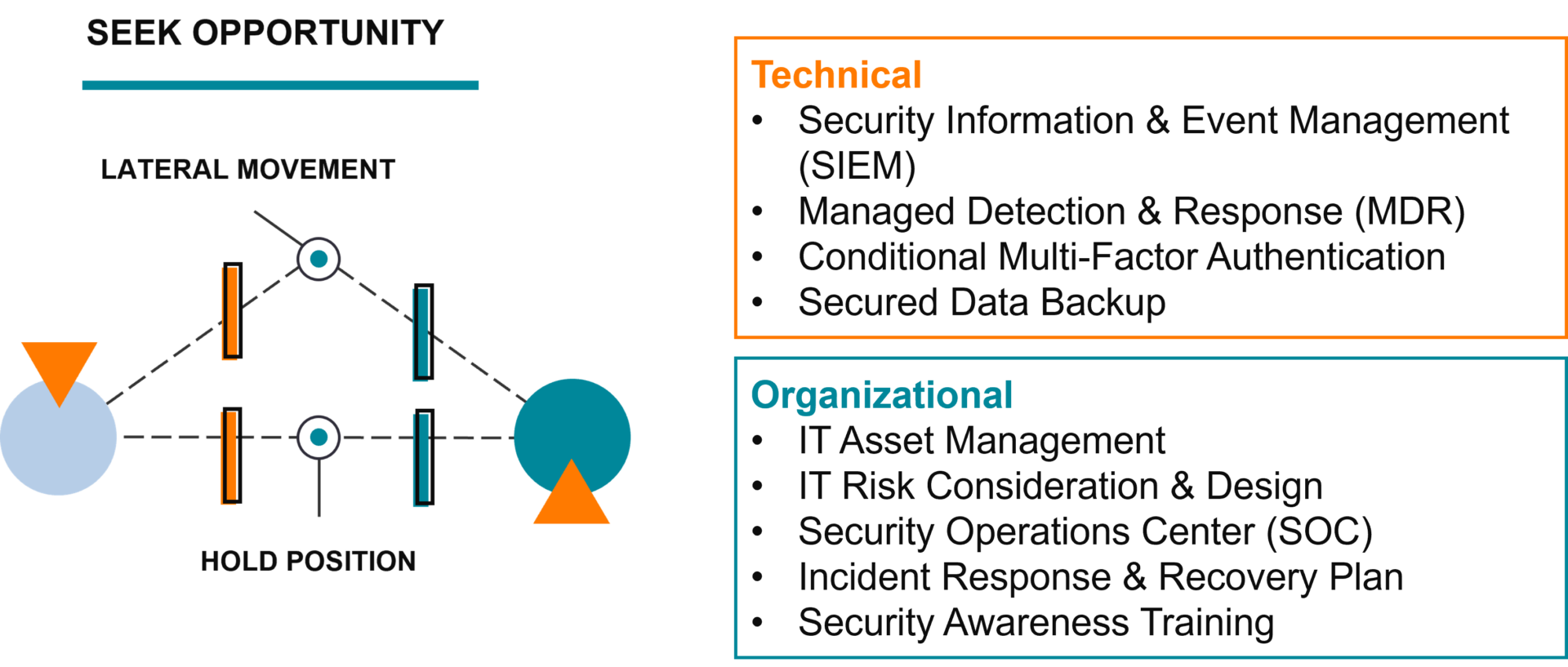
Seek Opportunity
Now that the threat actor is inside your environment; logged in with one of your organization’s user accounts, or using software they control to remotely execute commands, the threat actor will begin to seek opportunities. They will use discovery tools to probe the environment and see how far their access extends in your organization’s network and what information is valuable to you or others.
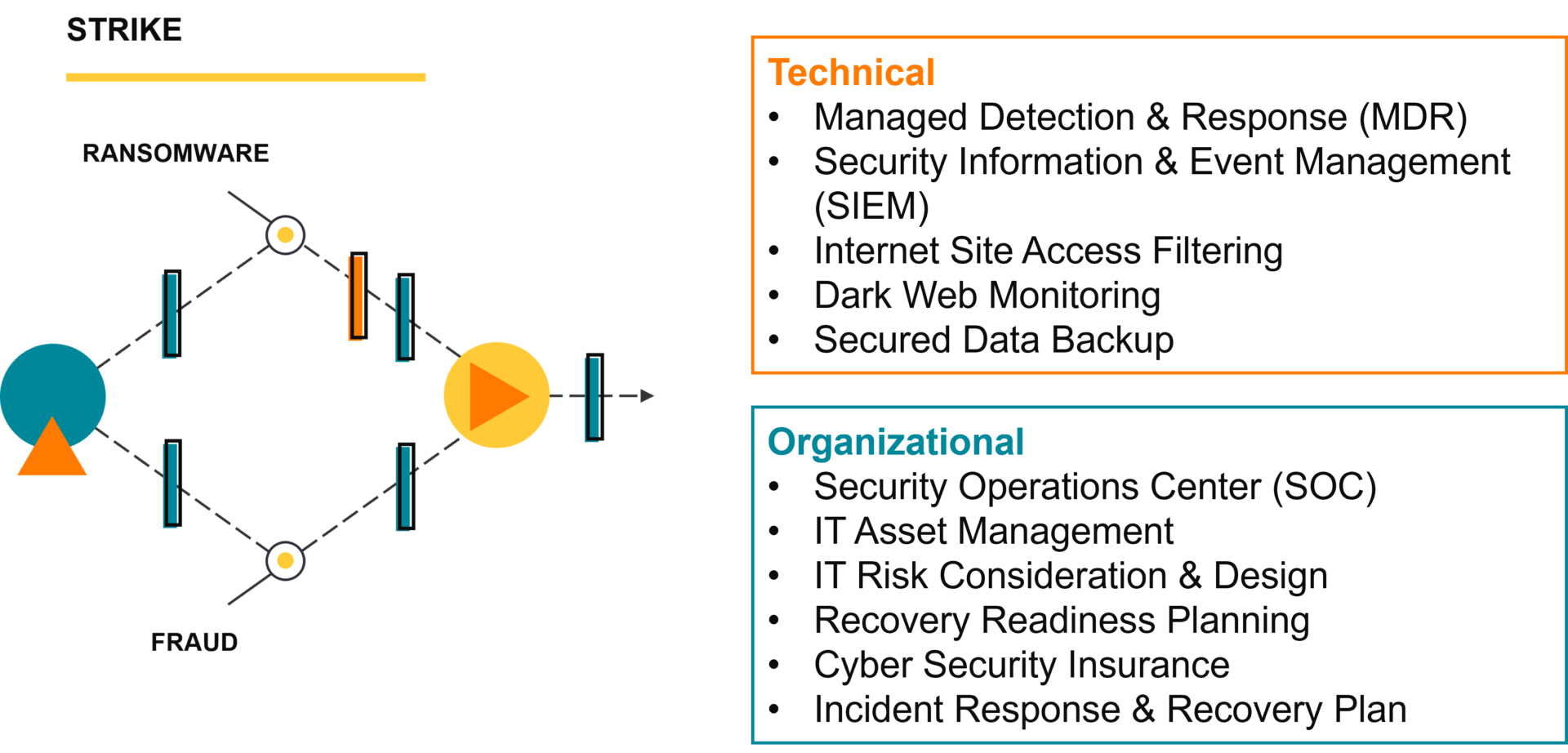
Strike
Once the threat actor believes they have found a valuable target, collected enough information to be convincing, or they believe they have been discovered, they will then launch the damaging portion of their attack, the strike. They will use your organization’s trust and relationships as a connection point to try to extend their reach into your vendors’ and customers’ environments, looking for the next opportunity.
Disrupting the Attack Chain
In a perfect world, there would be one security solution that would do it all to disrupt and protect, but unfortunately that does not exist. Every security tool or process has gaps. By layering tools and processes, you create additional opportunities to detect and stop the attacker – what one layer cannot detect or stop, the next layer might.
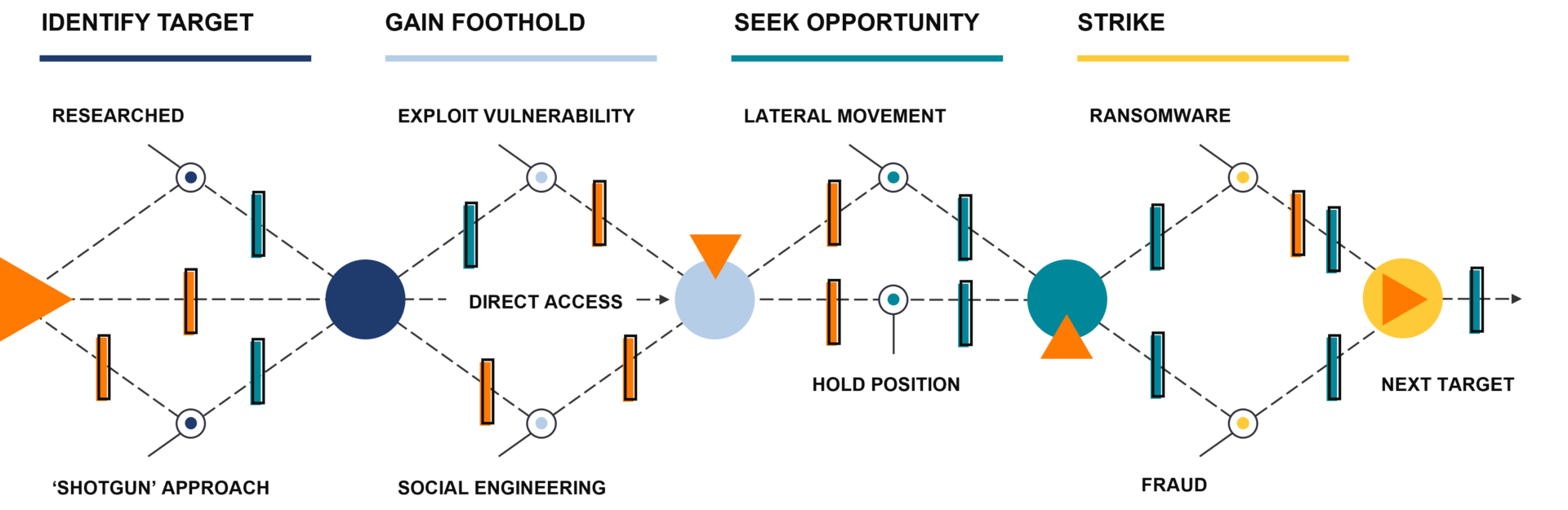
Layered Security Approach
By having these core security tools, your layered security approach will put potential barriers in the way during the attack chain. Some of the layers can log and detect certain types of unusual activity, some can help your organization users maintain awareness and vigilance for unusual activity. Others can automatically stop certain types of activity if it is monitored and managed. With a response plan, your organization becomes more resilient and able to manage risks. With a layered security approach, the attack chain will now have barriers where the previous gaps were available for compromise.
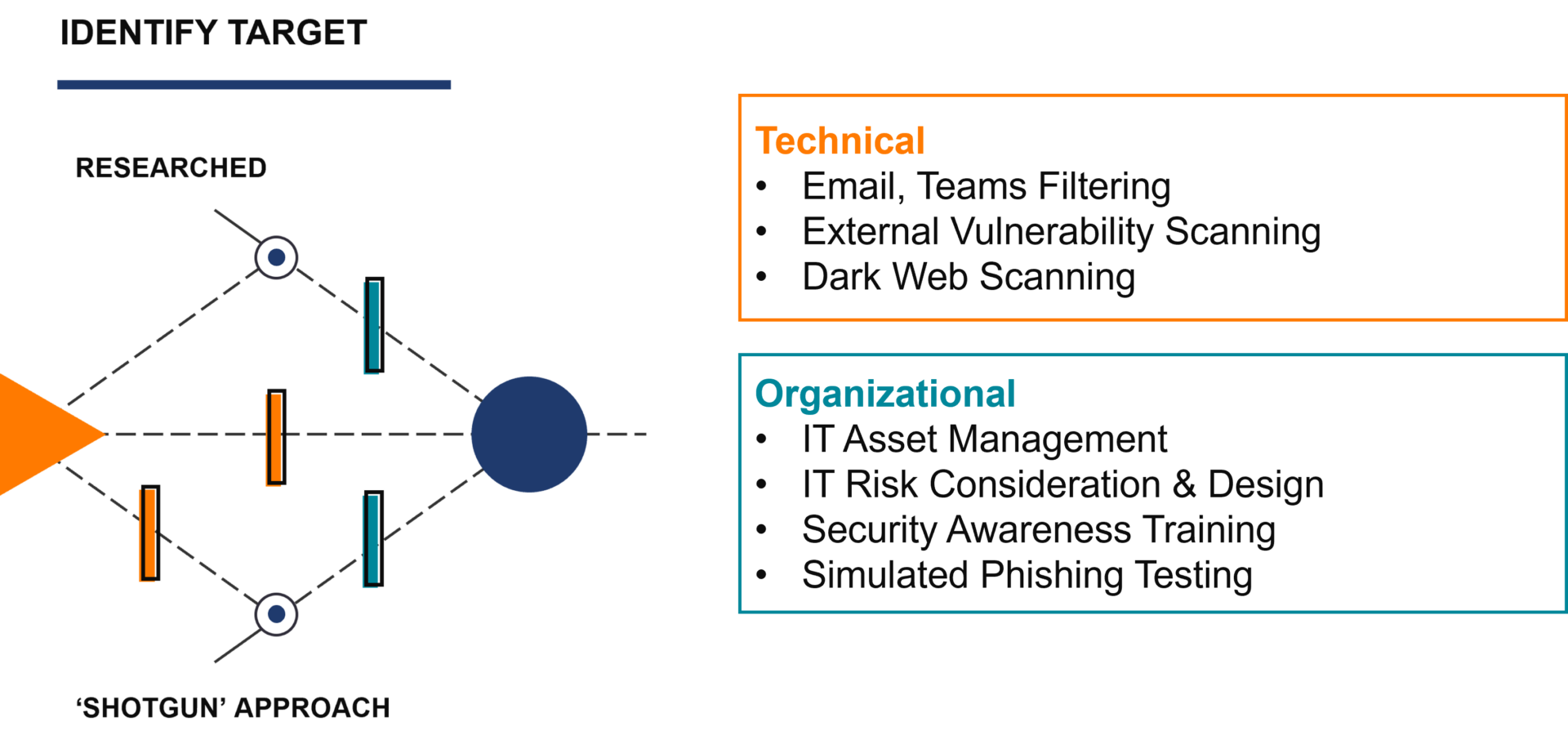
Disrupting Identify
To prevent your business from becoming a target in the first place, you need to reduce your attack surface. Your attack surface is your IT – all the doors that lead to your confidential data and systems. To reduce your attack surface, you must be aware of your IT assets, understand what vulnerabilities you have, and use a risk-based approach to remediate your vulnerabilities. On the organizational side, educate your team on security awareness best practices and test their training adoption with mock phishing emails. Creating a culture that is vigilant and mindful about security prevents your team from being an easy target for a shotgun-approach phishing campaign.
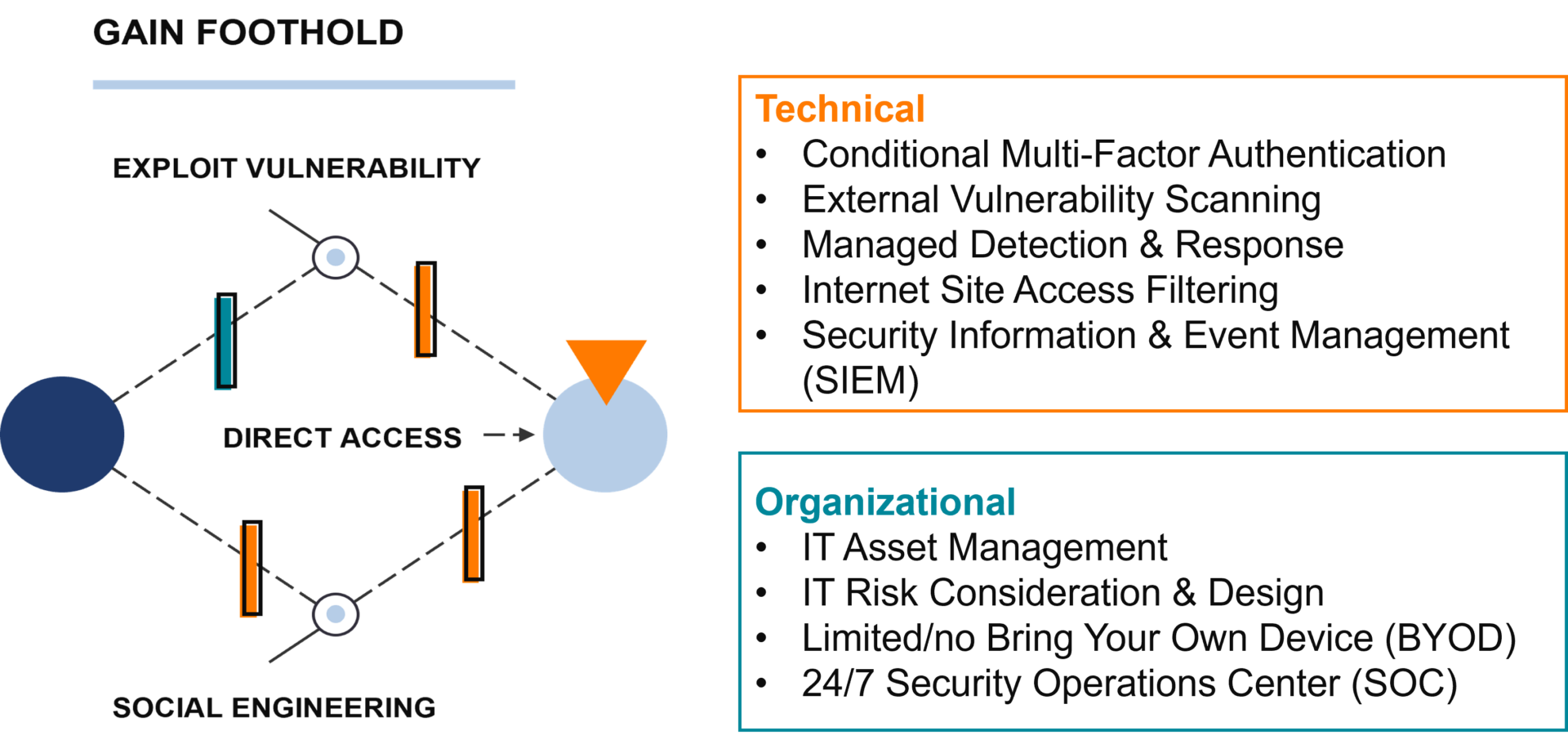
Disrupt Gain Foothold
Let’s say one of your people is successfully phished and they give away their corporate login credentials. By implementing multi-factor authentication, even if the attacker has their credentials, they won’t be able to successfully login. You can take that a step further and install Managed Detection & Response (MDR) on all your company devices. Even if the attacker were to successfully log in, MDR would send an alert to your security team that there is unusual activity on the compromised employee’s account.
Disrupt Seek Opportunity
Once an attacker is inside your environment, they will figure out a way they can extract the most value from your business. They may choose to exfiltrate your data and sell it or use it to compromise your clients/partners. Or they may install ransomware on business-critical IT systems and demand payment to restore access. You disrupt this stage of the attack by having visibility across your IT, that is where Security Information & Event Management (SIEM) comes in. SIEM can bring information across your environment into a single place, allowing your security team to detect suspicious activity and investigate it.
Disrupt Strike
The key to disrupting a strike is having a security incident response plan, and a Security Operations Center (SOC) to carry it out. Every second counts when you’re being attacked – you need a way to detect when a strike is occurring, a method to stop the damage, and the visibility to investigate the full extent of the breach. MDR and SIEM are tools your security team can use to disrupt a strike and investigate the attack to determine what recovery actions are necessary.
Let’s say you do everything right and you still get breached – it can happen. If you have a backup solution, your data is fine. If you have a good cyber insurance policy, then your business will be fine. If you’ve dedicated the time to understand your risks and create a plan for a breach, a successful attack will not be the end of the world.
Key Takeaways
- Cyberthreats are rising and your business will eventually be breached. You must plan for it ahead of time by implementing core security controls and developing an incident response and recovery plan.
- Security requirements are growing – every year we add new items to the core security control list. You must stay informed and remain vigilant to stay on top of an evolving threat landscape.
- Cyberattacks are not one event, but a long series of actions that can take place over days and sometimes weeks. You have an opportunity to disrupt the attack at many points along the chain to completely avoid, or at least minimize, the damage and disruption to your business.
- If you are attacked, report it to ic3.gov. Even if you do not need their help, you are contributing to their threat intelligence. Especially report it if you have wired away money, they have about an 80% success rate in recovering wire fraud funds.
If you need an IT partner that will help you prepare your business for today’s threats, visit our IT Security page to see how Aldridge can help!






