One of the best ways to make your online accounts more secure is by using Multi-Factor Authentication (MFA). We’ll explore three important aspects of MFA that can greatly enhance your online security.
3 MFA Best Practices for Microsoft 365
1. Use App-Based Challenge-Response Authentication
The Microsoft Authenticator app is not only free but also provides a secure and private way to enhance your account security. You can use it on your personal smartphone without worrying about your company accessing your personal data. It only shares your approximate location when you log in, and that too, with your permission. Unlike SMS messages, using this app for Multi-Factor Authentication (MFA) confirms that you’re logging in from your trusted smartphone. Furthermore, unlike traditional Time-based One-Time Passcodes (TOTP) that constantly change, MFA with the Microsoft Authenticator app proves that you have interactive access to your own phone, and it considers your location to assess login risk.
The Authenticator app offers various ways to confirm your identity, and the most secure one is called “challenge-response.”
Here’s how it works:
After you enter your username and password, the app will ask you to enter a simple two-digit code provided by the application or website you’re trying to access. Your smartphone, with the Microsoft Authenticator app installed, will notify you, and you’ll need to enter this code. If you’re not physically near the app or website, you won’t know the code, adding an extra layer of security. Additionally, the app will display the approximate location of the login attempt, so if it seems unusual or from a different place, you can reject it immediately. This method offers a unique combination of security, user-friendliness, and context that other authentication methods don’t provide.
2. Use Conditional Multi-Factor Authentication
Constantly requiring MFA can become frustrating for your users. This approach might even make your system less secure if users become too accustomed to simply approving MFA requests out of habit, creating an opportunity for threat actors to manipulate them into approving a malicious login. Some attackers send numerous MFA requests at odd hours, hoping that users will eventually give in due to fatigue.
Maintain Balance
It’s more practical not to interrupt users with MFA challenges when the risk is low. For instance, if users are accessing a routine application from a familiar location and device where you trust both the device and the location, and they know their password, this still counts as multi-factor authentication. In such cases, there’s no need to frequently or randomly challenge users with an additional MFA step.
The ”multi” in “multi-factor authentication” signifies the use of a mix of different elements:
- Something you know (like a password)
- Something you have (such as your smartphone or a familiar work computer)
- Something about you (like a biometric feature).
Conditional MFA allows you to adjust when you receive an extra challenge from your smartphone for authentication. This way, you don’t have to rely solely on your smartphone for every login, preventing user fatigue and maintaining security.
3. Use Frequent Challenges for High-Risk Authentications
One of the trickiest social engineering attacks to guard against nowadays is what’s known as the “Attacker-in-the-Middle” (AitM) attack.
How an Attacker-in-the-Middle (AitM) Attack Happens
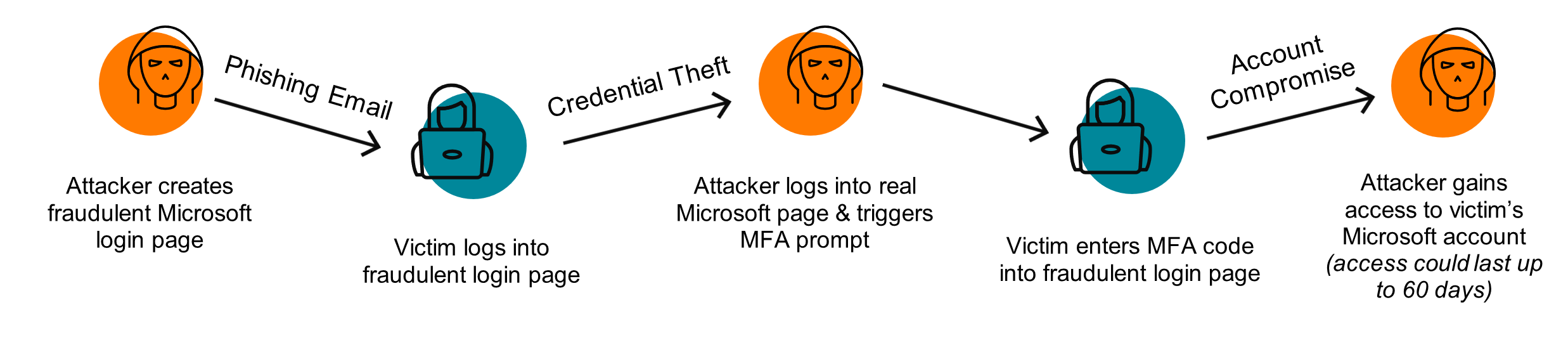
A malicious actor takes advantage of readily available tools to set up a new website on a web address of their choice, often selecting a domain name that closely resembles yours or Microsoft’s services. This deceptive site can even mimic Microsoft’s branding and logo, making it look legitimate. The attacker then employs various tactics, like phishing, to lure one of your team members into visiting this site, under the guise of routine business information access. The user encounters what seems like a normal Microsoft 365 login prompt, which they expect in this context, and they proceed to complete it, including multi-factor authentication. Unbeknownst to them, the attacker’s website acts as an intermediary between the user and Microsoft, capturing the successful authentication, termed a “session.” The attacker can then exploit this session without needing to know the user’s password or MFA, at least until the session expires.
By default, many sessions won’t expire for days, meaning the threat actor – if they’re fast – can now use that compromised session to browse your user’s mailbox, OneDrive, SharePoint, and account preferences. Most threat actors use automated websites to try to collect sessions, and review captured sessions 6, 10, 24, or sometimes even 48 hours later.
Start Working Towards Better Security
You should not be worried whether you’re secure. Partner with Aldridge and become confident that you’re prepared for whatever happens next. Take a look at our IT Security page to see how we can help.






