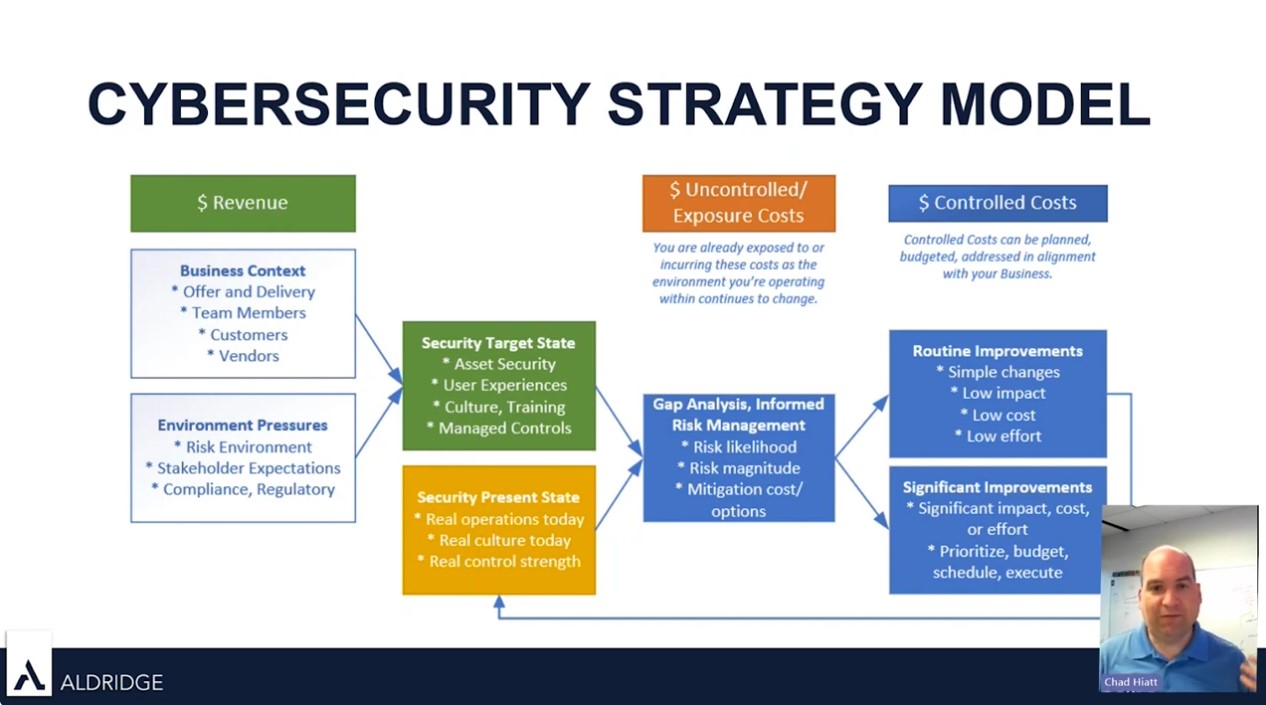
Three crucial areas are currently shaping the future of security best practices. These insights are pivotal for businesses striving to enhance their cybersecurity posture.
3 Security Best Practices for Today’s Threats
Growing Compliance Requirements
One significant trend is the increasing complexity of compliance requirements. Businesses across various sectors—whether dealing with the federal government, healthcare, specific states, or seeking cybersecurity insurance—are facing higher standards. These compliance mandates ensure that organizations are not only maintaining strong cybersecurity measures but are also prepared to respond effectively to incidents.
Compliance is no longer just about checking boxes. It’s about demonstrating proactive cybersecurity measures to minimize risks to all stakeholders. This evolving landscape means businesses must continuously update their practices to meet these standards. Failing to do so could result in severe repercussions, including financial penalties and loss of business trust.
Importance of Software Bill of Materials (SBOM)
The concept of a Software Bill of Materials (SBOM) is gaining traction as a critical defense against supply chain attacks. Recent incidents have shown how threat actors target businesses by infiltrating software vendors. Instead of attacking a business directly, they exploit vulnerabilities in the software supply chain.
An SBOM provides visibility into all the components that make up a software application, including those from third-party vendors. This transparency is crucial for identifying and mitigating vulnerabilities that could be exploited in supply chain attacks. By knowing exactly what’s in their software, businesses can better defend against these sophisticated threats and ensure they are using secure, up-to-date components.
Shifting Towards Integrated Security Tool Suites
Another key development emphasizes the need for businesses to elevate their security maturity by adopting a layered approach with integrated tool suites. Traditionally, the focus was on finding the best individual tools for specific security tasks. However, as threats become more complex, relying on different tools managed separately will no longer cut it.
Today’s approach should consist of selecting security tools that work cohesively within a unified framework. This means choosing suites of tools that offer compatibility, allowing for a single pane of glass for management and policy enforcement. This shift towards integrated solutions reduces the complexity of managing multiple tools and enhances the ability to respond to threats consistently and effectively.
Embracing these evolving best practices is not just about meeting current standards but about futureproofing your organization’s security posture. As cyber threats continue to evolve, so must our strategies and tools to defend against them.
WATCH THE FULL VIDEO
Aldridge’s CTO, Chad Hiatt, talks on cybersecurity updates and the ‘Right of Boom’ concept. Watch the full video to see how you should be thinking about security, gain valuable perspectives on the evolving LOTL threat landscape, learn about the new best security practices of 2024, and using a cybersecurity strategy model for success.