As cyberthreats continue to evolve, business leaders are increasingly turning to solutions like Security Operations Centers (SOC) and Security Information and Event Management (SIEM) to stay ahead. You’ve probably heard these terms before, and you might even be considering implementing them in your own organization. But before you make any decisions, it’s crucial to understand what these security controls are, how they differ, and why using them together creates a stronger, more effective defense against modern cyber threats.
What is Security Information and Event Management (SIEM)?
Security Information and Event Management (SIEM) is a cybersecurity solution that collects and centralizes data from across your company’s IT environment, including applications, servers, and network hardware. By providing real-time analysis and generating alerts on suspicious activities, SIEM helps businesses quickly identify and respond to potential threats. SIEM works by:
- Integrating with your IT systems to monitor and gather data from multiple sources, such as applications, servers, and network devices.
- Streamlining security data from these systems into one platform, making it easier to spot correlations and identify anomalies.
- Providing a centralized source for security investigations, allowing your team to efficiently track, analyze, and investigate indicators of compromise, enabling them to respond faster and more effectively to threats.
- Retaining logs over time, which is essential for understanding the full scope of an incident. This long-term log retention allows your team to trace an attack’s origins and understand how it unfolded, ensuring a thorough investigation and recovery.
Without a SIEM solution, your security team might be limited to analyzing logs from individual applications, leaving critical blind spots. SIEM offers a bird’s-eye view of security events across your entire IT environment, empowering your team to detect emerging risks and thoroughly investigate security incidents.
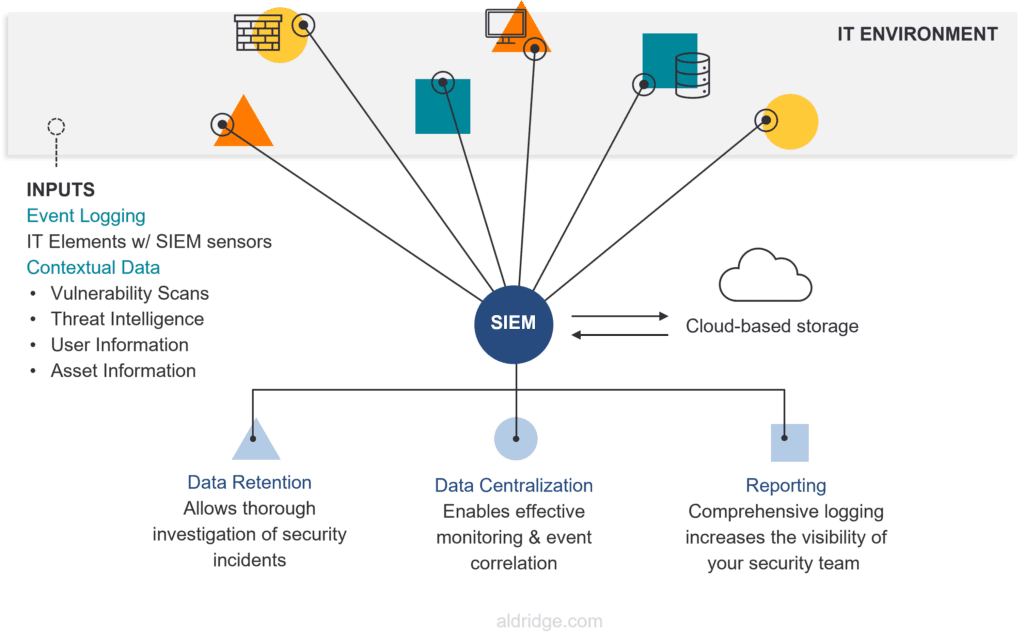
How Security Information & Event Management (SIEM) collects data, and the benefits of having a SIEM tool.
What is a Security Operations Center (SOC)?
The Security Operations Center (SOC) is a centralized hub responsible for monitoring and responding to security incidents across an organization. Unlike SIEM, which is a tool that collects and analyzes security data, the SOC is a team of experts—including analysts, engineers, and incident responders—who use tools like SIEM to detect, investigate, and respond to potential cyberthreats.
The SOC leverages the data provided by SIEM to monitor network activity, identify suspicious patterns, and manage security incidents. A key advantage of the SOC is its ability to provide continuous monitoring, using both human expertise and automated systems to track threats in real-time. This means the SOC can quickly assess the severity of incidents flagged by the SIEM and take appropriate actions to mitigate risks, such as isolating affected systems or initiating recovery protocols.
SOC teams don’t just rely on alerts—they perform proactive threat hunting, looking for vulnerabilities and patterns that might indicate future risks. They also continuously refine security controls based on the evolving threat landscape, ensuring that the organization’s defenses are up to date.
When SIEM and SOC work together, they create a fluid, efficient defense. The SIEM gathers and correlates data across the IT environment, while the SOC team provides the necessary context, expertise, and response actions. The quality of the data from the SIEM directly influences the effectiveness of the SOC, and together, they offer a robust approach to handling both known and emerging threats
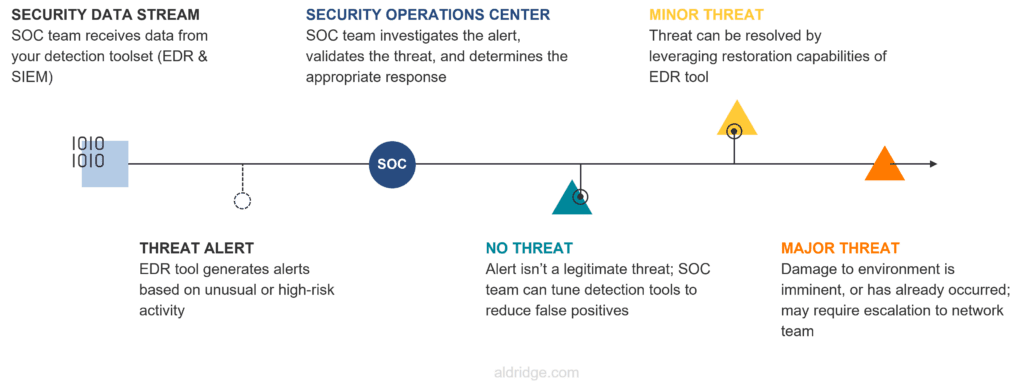
How a SOC team investigates security indicators using SIEM.
How to Get Started With SOC and SIEM
The foundation of any successful security strategy begins with alignment between your business and IT leadership. It’s crucial to establish clear goals, set realistic expectations, and commit the time and resources necessary to effectively implement and maintain SOC and SIEM solutions. This ongoing commitment ensures your organization is fully prepared to stay ahead of evolving cyber threats.
We understand that maintaining this level of security can be challenging, which is why our SOC and SIEM services are designed to make it easier for you. With our team of experts handling the complexities, you gain access to enterprise-grade security without the burden of managing it in-house. Let us provide the resources and expertise you need to protect your business—click here to learn more about how we can help.







