Understanding how threat actors plan and execute their attacks is crucial in strengthening our defenses and protecting against potential breaches.
Unmasking the Dark Art: How Cybercriminals Plan Their Attacks
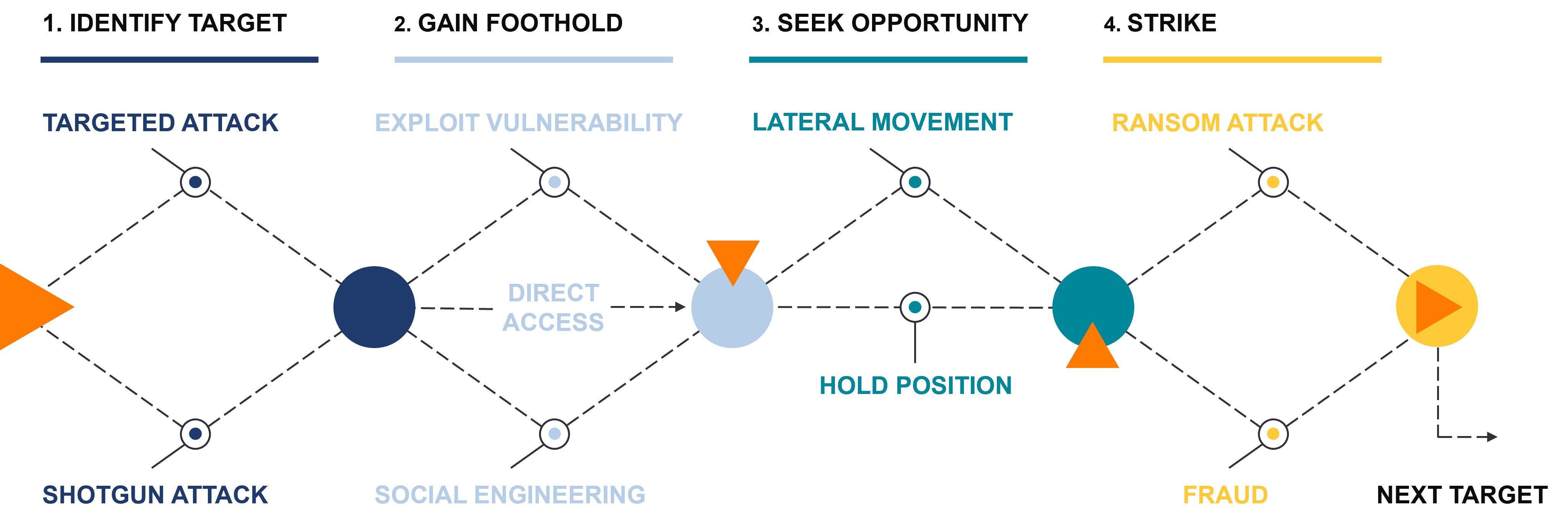
How Cyber Attacks Work
Step 1 Identify Target
There are two main approaches cybercriminals use to select their victims:
- Targeted – Attacker goes after a specific organization, conducting research on their tools, vendors, and people to construct a highly targeted spear phishing campaign or exploit identified vulnerabilities in their IT.
- Shotgun – Attacker launches a mass phishing email campaign on thousands of companies, only needing one or two people to fall for it and give up their credentials – providing the attacker access into the victim’s email and organization.
Step 2 Gain Foothold
The threat actor has successfully breached an email/account or exploited a technical vulnerability to gain access inside their targeted organization’s IT environment. This initial access point is crucial as it provides the attacker with a starting point from which they can further explore the target environment, expand their control, and carry out their intended objectives.
Step 3 Seek Opportunity
The attacker will use the visibility and access they gain from their initial foothold to identify how they can extract the maximum amount of value from their attack. This is referred to as a lateral movement – using their initial privileges and newfound access to information to further exploit their target organization.
Step 4 Strike
An attacker may hold their position for months, waiting for a good opportunity to escalate the attack and strike. Maybe the attacker has access to an employees’ email and identified an exploitable financial conversation, such as renewing an expensive tool or service. The attacker will wait for an email containing an invoice to come through that they can intercept and alter, tricking the employee to wire money to the attacker’s bank instead of the vendor.
The Anatomy of Cybercriminals
Cybercriminals come from diverse backgrounds, utilizing a range of skills and resources to carry out their attacks. Some work alone, while others operate in sophisticated groups or organizations, sharing knowledge and tools.
Defending Against the Dark Arts
Understanding the strategies employed by cybercriminals is the first step in building robust defenses. Here are essential measures to safeguard against potential attacks:
- Educate and Train: Regular cybersecurity training for employees is crucial to recognize and thwart potential threats, especially social engineering tactics.
- Implement Robust Security Measures: Employ strong firewalls, encryption, multi-factor authentication, and regularly update software to mitigate vulnerabilities.
- Continuous Monitoring and Response: Invest in systems that detect anomalies in network traffic, enabling quick responses to potential breaches.
- Backup and Recovery Plans: Regularly backup data and develop recovery plans in case of successful cyberattacks.
Tips to Stay Secure
- Don’t use your company login credentials on 3rd party websites, they could have a data breach and expose your credentials to the world
- Be vigilant every single time you’re asked to share protected information or make a financial decision, no matter who you’re talking to
- Don’t install “grayware” on company devices, and don’t work from devices that your kids use
- When working from a personal device…
- Don’t save protected information (work logins, client data, etc.) on the device itself
- Use the web versions of your tools whenever possible
Call to verify when…
- You get updated banking information
- Asked to do something unusual, urgently
- You receive an email that your account has been compromised
Resources
Learn how to protect your business:
- https://www.cisa.gov/ “America’s Cyber Defense Agency”
Learn about the threat landscape:
Learn the basics:
The world of cybercrime may seem perplexing, but translating the methods used by cybercriminals is pivotal in fortifying our digital landscapes. By understanding their strategies, we empower ourselves to create a safer and more secure digital environment.
Protect What You’ve Built
Security doesn’t stop moving – there is always some new threat or acronym you need to know about. Visit our IT Security page to see how Aldridge can help you start working towards better security.






