Today, customer trust is no longer rooted in a strong gut feeling and someone’s good word. In every industry, data is key to delivering and optimizing customer service delivery. Business leaders are responsible for protecting a breadth of sensitive information that can have serious cost consequences and legal penalties if compromised. Effectively managing IT security can be a challenge for growing companies that experience frequent changes to their teams and operations. Business leaders need a cyber security strategy to have a clear picture of where to invest in mitigating threats over time successfully.
IT Security Challenge: Balancing Cost, Risk, & Productivity
Chief Financial Officers (CFOs) focus on providing the leadership to drive their organization’s strategy, operations, and controls while balancing productivity, risk management, and investment costs along the way. For the modern CFO, technology investments around AI and data management are now critical pieces of a business’s continuity and growth strategy. These efforts require expert consulting and resources to execute effectively.
IT Security & Hybrid Work: Your People Are Your #1 Risk
Today’s hybrid workforce of remote and in-office employees presents another challenge for business leaders: balancing security and remote work productivity. According to Datto, ransomware remains the number one malware threat facing businesses in 2021. In 2020, the top three vectors for a successful ransomware attack were:
- Phishing at 54%
- Poor Employee Practices at 27%
- Lack of Employee Cyber Security Awareness Training and Testing at 26%
The common denominator? People. Hackers are evolving their tactics to exploit human vulnerabilities with targeted social engineering schemes and fraudulent requests. In other words, your approach to IT security will undoubtedly fail to protect your business if its dominant focus is technology. 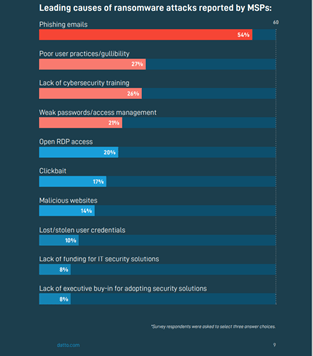 IT security is just as much about managing people as it is about managing technologies like cloud security and data backups. Your people can be your strongest cyber security defense or your greatest weakness, depending on the level of training and continued education they receive. It takes a continually iterative, strategic approach to mitigating the risks of the inevitable cyber attack. It’s becoming easier for hackers to execute a successful attack as they’re becoming easier to replicate and require less technical expertise to execute. In this article, we will cover what you need to know about today’s cyber security landscape and how your business can mitigate risks and their associated costs.
IT security is just as much about managing people as it is about managing technologies like cloud security and data backups. Your people can be your strongest cyber security defense or your greatest weakness, depending on the level of training and continued education they receive. It takes a continually iterative, strategic approach to mitigating the risks of the inevitable cyber attack. It’s becoming easier for hackers to execute a successful attack as they’re becoming easier to replicate and require less technical expertise to execute. In this article, we will cover what you need to know about today’s cyber security landscape and how your business can mitigate risks and their associated costs.
Security Awareness Training: Easily Reduce Human Risk
The KnowBe4 2020 Phishing By Industry Benchmarking Report reported that an average of 37.9% of untrained employees will click on a simulated phishing test link.
Without the knowledge and training to recognize a phishing attack, one-third of the average workforce is likely to unknowingly jeopardize their company’s security with one click.
When you consider the number of phishing emails and targeted vishing attacks targeting your employees, your chances of a breach rise exponentially. After 90 days of cyber security awareness training and routine phishing tests, the number of at-risk staff dropped to 14.1%. And after one year, to less than 5%, for an 87% improvement across the board after one year or more. For cyber security awareness education and training programs to be effective, you must invest the necessary employee time and company resources. In addition, the effort to build an aware and engaged culture is much like a marketing campaign. It often involves an ongoing, comprehensive training solution that is both iterative and responsive to the shifting cyber threat landscape. We provide our clients with simulated phishing training and testing software capable of pinpointing at-risk employees and delivering targeted education and testing programs to address these vulnerabilities. Learn more about building a culture of cybersecurity awareness using employee education and training programs by reading our blog, How to Protect Your Business from Social Engineering Attacks. Or check out our infographic, Employee Security Awareness Training and Best Practices.
Cyber Security Incident Response Plan: Minimize Impact
Many businesses understand the importance of IT security threat prevention but fail to plan for and refine their cyber security incident response strategy. The goal is for your business to never pay a ransom or suffer irreparable damage from an attack. A cyber security incident response plan accounts not only for targeted, malicious attacks but for common employee mistakes like data deletion, data loss, accidental data leaks, and more. Regardless of the intent, any threat to your company’s data security can result in significant business downtime, legal ramifications, and financial penalties. While data breaches are not the only type of data security risk organizations need to address, they are often the most visible to the public eye and can put a dent in your hard-earned reputation. According to Datto’s 2020 report, 78% of Managed IT Services Providers reported ransomware attacks on their clients over the past two years, and 92% of MSPs anticipate these attacks will continue in the next year. You can work with your IT services provider to create a plan capable of preventing, responding to, and recovering from a cyber attack. A response plan is especially relevant today, considering that the average cost of downtime following an incident increased by 94% from 2019 to a total of $274,200 for the average cost of downtime in 2020.  Downtime and lost productivity can hinder business goals and put sensitive, business-critical information in harm’s way. These risks can damage your company’s reputation and break the hard-earned trust of the clients and partners you work with. Your business needs a team of security professionals with the technology tools and business expertise to prevent, predict, and prepare for potential IT security risks with minimal business disruption. Learn more about creating a cyber security incident response plan by reading our blog, How To Prepare Your Business For a Cyberattack.
Downtime and lost productivity can hinder business goals and put sensitive, business-critical information in harm’s way. These risks can damage your company’s reputation and break the hard-earned trust of the clients and partners you work with. Your business needs a team of security professionals with the technology tools and business expertise to prevent, predict, and prepare for potential IT security risks with minimal business disruption. Learn more about creating a cyber security incident response plan by reading our blog, How To Prepare Your Business For a Cyberattack.
Information Security Planning: Establish Customer Trust
Technology is becoming increasingly integrated into everything we do. As a result, customers expect your business to protect this information with a reasonable level of proactive IT security defenses, response planning, and policy compliance in exchange for their data. The 2019 Norton LifeLock Cyber Safety Insights Report Global Results found that four out of five individuals felt they had lost control of their data and how businesses use it. However, two out of three people reported they are proactively looking for ways to improve their personal privacy and security. Consumer trends and rapid technological innovation have transformed how both B2B and B2C companies build business relationships and consumer trust. Now, this trust depends on the product’s value and how well your business can mitigate the risks of everyday exchanges. Routine business transactions can be exploited as attack vectors for hackers when executed without the right level of security technology, processes, and human defenses. Cybercriminals can target:
- credit card payments
- client financial requests
- accessing and sharing sensitive customer information
- storing business-critical data in the cloud
- and more
An information security strategy drives business resilience and directs your approach to risk and security governance. Learn more about data governance and what an effective approach covers by reading our blog, What is Data Governance?
Information Security Program: Evolve with Consumer Demands
As the value of customer privacy increases, so does the pressure on companies and their IT and third-party vendors. Businesses that prioritize proper data governance and cyber security best practices differentiate themselves from their competitors by providing consumers with peace of mind that their information is protected. However, without the support of a capable IT partner, it can be time-consuming and divert internal resources from your core business. A capable managed IT services provider can help you manage your data security efforts as they manage the security of their own network. We understand that our clients’ business health and longevity depend on the safety of their sensitive data and information technology systems. That’s why we invested in becoming SOC 2 Type 2 certified and can provide our clients with hard evidence that their business is in good hands. Learn more about what it takes to become SOC 2 Type 2 certified and how this standard helps uphold data integrity and security for our own organization and our clients’ businesses by reading our blog, What is SOC 2 Type 2 Compliance & Why Your IT Provider Should Have It.
Is It Time to Take a Second Look at Your Cyber Security Strategy?
If your managed IT services provider is not working with your leadership team to continually improve your IT security position, they aren’t the right partner for your business. Get a second opinion from a third-party IT consultant to better understand where you stand today and what you need to do to move forward. We provide our clients with the cyber security services they need to balance security and productivity in a sustainable and cost-effective way. IT security applies to all principles of the Aldridge Framework for Successful IT, but it cannot stand alone. The right IT strategy, design, implementation, and support resources are crucial to implementing a cyber security roadmap for optimal business resilience. We apply our Framework for Successful IT approach to all aspects of our outsourced IT services and consulting. Learn more about how our team can help you understand your IT security needs and goals and schedule time to speak with an Aldridge team member today.







