Email compromise is a clever and widespread technique used by cybercriminals to breach the security of both individuals and organizations, in fact, email compromise is the most common & costliest breach to date.
Related | Email Compromise: The Most Common & Costliest “Breach”
Given that we often share sensitive information through our email accounts, it’s crucial to grasp how these compromises take place.
How Cybercriminals Compromise Your Business Email
An email compromise is a sophisticated cyberattack that targets individuals, businesses, or organizations.
- The process typically begins with the cybercriminal conducting thorough scouting, gathering information about the target.
- With this intelligence, they craft convincing phishing emails tailored to the target’s interests and habits, often impersonating a trusted contact, executive, or service provider. The email might contain urgent requests for sensitive information, financial transactions, or credentials.
- Email compromise can lead to severe consequences, including financial losses, data breaches, and reputational damage.
Here’s an example:
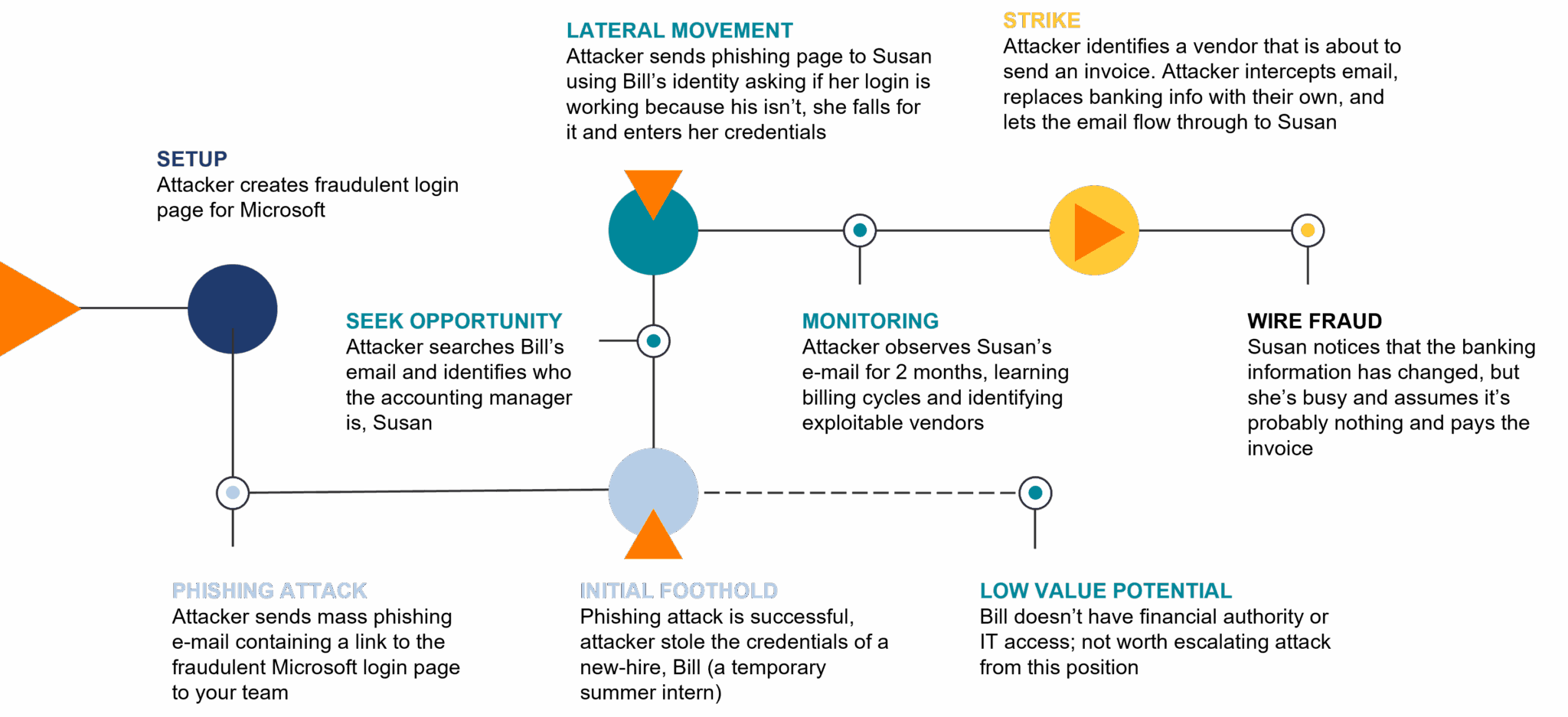
Identify
The cyber attackers chose to make a fake Microsoft login page because so many people and organizations use Microsoft products or are familiar with them. Microsoft is a big name in the tech world, and people tend to trust it. By creating a fake login page that looks like Microsoft’s, the attacker hoped that people would be tricked into sharing their personal information. This kind of trick is sadly common in today’s online world, where bad actors take advantage of the trust we have in well-known companies like Microsoft.
Gain Foothold
The attacker initiated a large-scale phishing campaign targeting hundreds of companies, with the objective of successfully tricking just one individual who lacks Multi-Factor Authentication (MFA) or any additional identity protection measures.
Seek Value
The cyber attacker managed to get into an intern’s email account, but since there wasn’t much valuable information there, they decided to use the intern’s identity to dig deeper into the organization’s systems and target the accounting manager. This tactic of hopping from one point of access to another is known as “lateral movement.”
Strike
The attacker patiently lurked in Susan’s inbox for two months, biding their time for the perfect moment to act. They established a rule to intercept invoices from a vendor, made alterations to the banking details, and then allowed the modified invoice to reach Susan’s view. Without much suspicion, she proceeded to make the payment, leading to an unexpected case of fraud.
Email compromise is not just something theoretical – it’s a real threat that’s always around. You can protect yourself by learning about how it happens and using strong security habits. Being aware of suspicious things, using good online practices, and being careful about what you share can help stop cybercriminals from causing trouble. Discover all four crucial security concepts that will empower you to protect yourself in our Security Awareness 101 [4 Concepts You Must Know] blog.
WATCH THE FULL WEBINAR
Discover the latest insights, best practices, and proactive measures that can safeguard you and your organization from potential threats. Watch our full Security Awareness 101 webinar now and take your security awareness to new heights with guidance from our seasoned professionals.






