Hackers continue to evolve their attack methods to take advantage of weaknesses in the external network of governments and organizations around the globe. External vulnerability scans check the surface area your network presents to the world and the larger internet. They are essential to taking a proactive IT security approach to protect your business from cyber threats.
We will explore how external scans work, the benefits of leveraging them routinely, and why they are essential to understanding and mitigating your network perimeter’s risks.
What Is External Vulnerability Scanning?
An external vulnerability scan looks at your network through the lens of a hacker. This approach scans external IP addresses and domains to search for vulnerabilities within your internet-facing infrastructure. By doing so, you better understand the strength of your externally facing services. You can identify:
- Vulnerabilities within your perimeter defenses
- Ports open and exposed to the internet
- Any threats accompanying new servers or services
How External Network Threats Impact Your Business?
An external vulnerability scan detects potential vulnerabilities within your organization’s perimeter security or cloud-based applications that an internet-based attacker can exploit to access or interrupt your network. Such attacks often lead to:
- Business disruptions and downtime
- Damage to or inability to access business-critical systems and/or data
- Stolen privileged or proprietary information (e.g., financial information, client data, IP, etc.)
- Deployment of malware used to exploit an organization, long-term
- Abuse of an organization’s trust and credibility by hackers to exploit its customers and vendors
External Vulnerability Exploit Example: Security Cameras
Let’s say your business has a security camera system that is open to the internet so that you can view the camera feed remotely using an app. An attacker could exploit a vulnerability in your camera system (ex log4j) to gain visibility into your network. With that visibility, the attacker identifies a weakness that will give them access inside your network.
Once the attacker has an established foothold inside your network, there are a few things that can happen. They can perform a lateral movement, using their current access and privileges to compromise a different system or account that has a higher value potential. Or perhaps the attacker is already in a good position inside your environment and wants to sit and watch. They will monitor your activity, looking for exploitable processes or users. Once a good opportunity presents itself, the attacker will make their move. There have been instances where attackers have been inside a victim’s environment for years before acting.
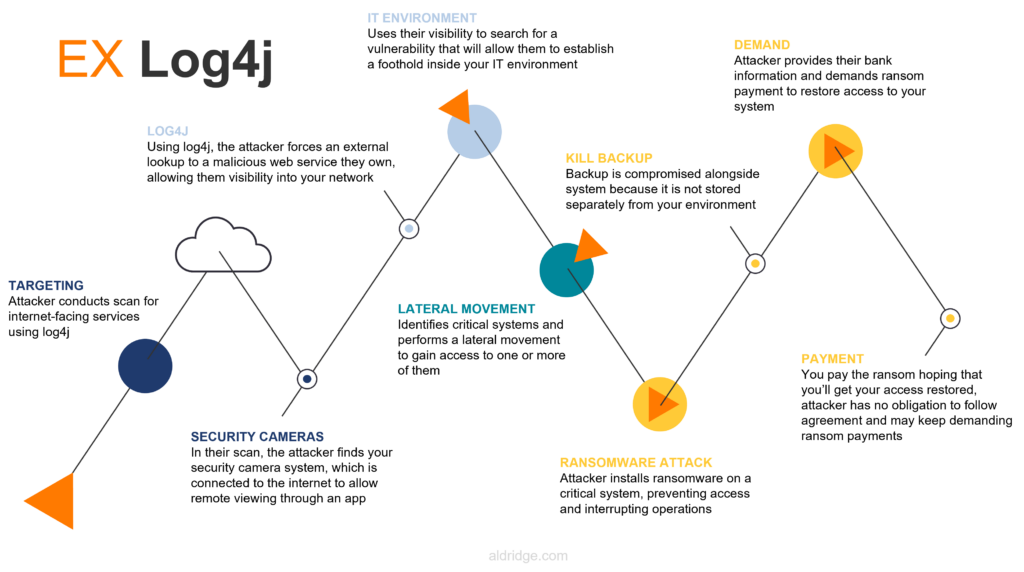
Visual representation of a log4j exploit of an internet-facing security camera system
The lesson here is that even seemingly innocuous things like an internet-enabled security camera can be used as a jumping-off point for a large-scale attack. Routinely conducting external vulnerability scans to identify those internet-facing devices and remediating any major risks is necessary to keep your business protected.
Benefits of External Vulnerability Scans
How often your organization should conduct external vulnerability scans depends on your unique risk tolerance and compliance needs. It is important to work with a qualified team of IT security and consulting experts with the resources to generate and deliver a report showing:
- Internal network IP addresses
- Active listening network services were detected for each address
- Active, high-risk network service security vulnerabilities for priority remediation
External vulnerability scans provide detailed insights into the weaknesses of your network perimeter that can lead to a potential IT security incident. Routine scanning is also key to maintaining an up-to-date list of the new servers or services added to your network and any potential threats that may accompany these additions.
By running routine external vulnerability scans at an appropriate cadence, your organization can keep track of new IP addresses and services. It can also build a formal process for validating the approval and security of any implemented anomalies discovered.
We help our clients discover and strategically address their external network vulnerabilities. Our external vulnerability scan service is designed to meet your organization’s unique security and compliance needs. Visit our Small Business Managed IT Cybersecurity page to learn more about how we can help protect your business and schedule time to speak with a member of our team.






