Cybercriminals have perfected the art of deception, creating sophisticated traps that can trap even the most cautious of users. As we navigate the internet, it’s crucial to arm ourselves with the knowledge and awareness necessary to recognize phishing attempts and their subtle red flags.
Protect Yourself from Phishing (5 Red Flags to Watch for)
Phishing Red Flags
- Unknown sender, or known sender contacting you a new way
- Poor grammar and spelling
- You’re being asked to provide protected information
- Strange links or unexpected attachments in the email
- Sense of urgency – you must react now
Here’s examples of real phishing attacks so you can better understand how to recognize when you’re under attack.
Example 1 of a Mass Phishing Email:
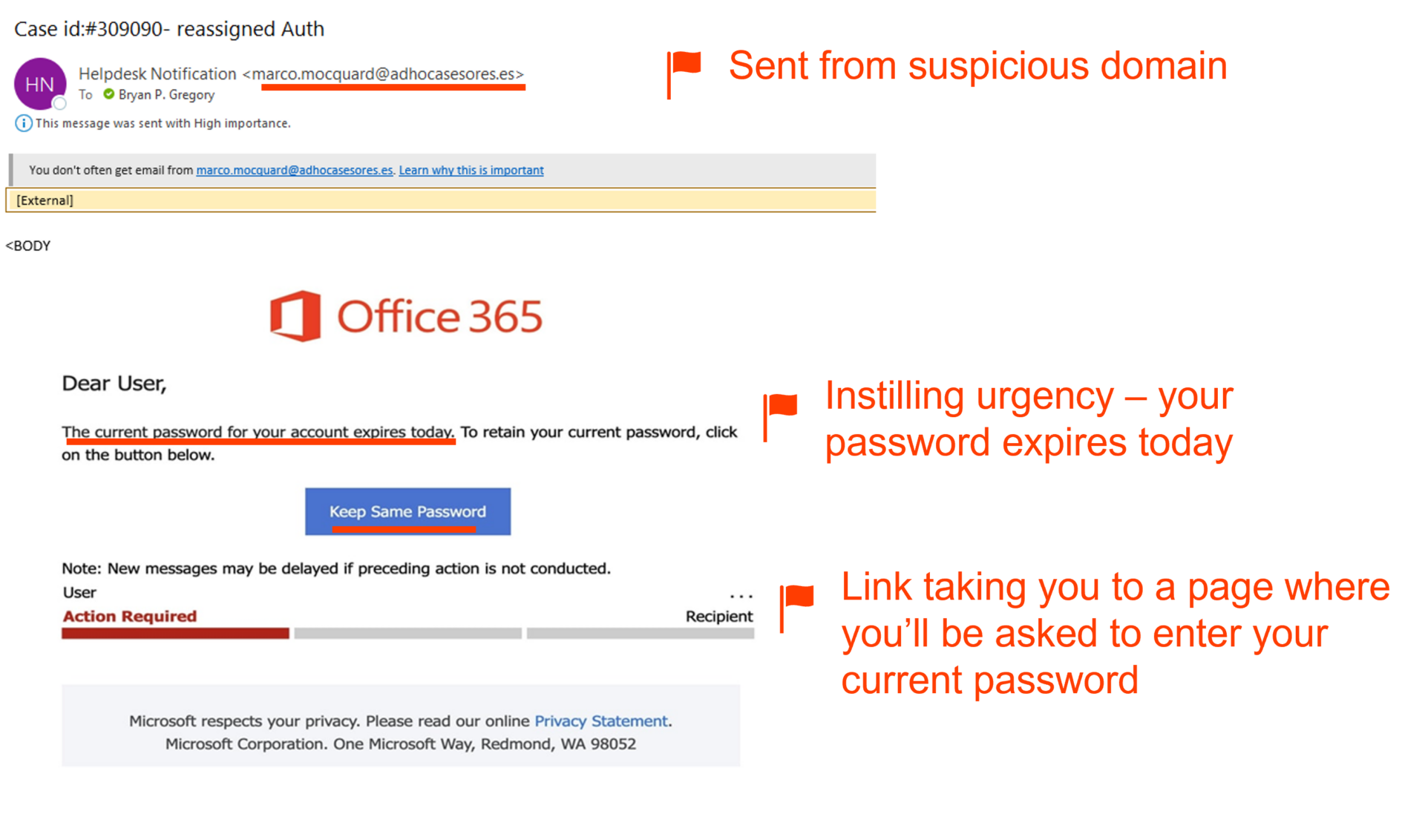
If you receive an email from an unfamiliar or strange-looking email address, it’s a sign that something might not be right. Similarly, if the email is trying to make you feel like you must do something quickly, it’s usually a trick to make you act without thinking too much. This rush can make you miss important clues that the email might not be real. Lastly, the presence of a link within the email that directs recipients to a page requesting their current password is a clear sign of phishing. Legitimate organizations typically don’t ask for sensitive information through email and would direct users to secure channels for such requests. These combined red flags strongly suggest that the mass phishing email aims to deceive recipients into exposing their personal information and should be treated with caution to avoid falling victim to the scam.
Example 2 of a Mass Phishing Email:

If the email doesn’t come from a specific person and doesn’t use the official domain of a trusted organization, it raises doubts about its legitimacy. These emails often use generic sender names and addresses that don’t match the usual communication style of legitimate sources. Additionally, if the email includes an attachment or document that you weren’t anticipating or have no prior knowledge of, it’s wise to use caution. Cybercriminals frequently attach files or links disguised as harmless documents, attempting to infect your device with harmful software.
Example of a Spear Phishing Email:

Source: Tessian
These phony website addresses are made to look real, fooling you into thinking the email comes from someone you trust. Also, if the email makes you feel like you must do something right away, it’s meant to make you act fast without thinking much. But this hurry can make you not notice possible problems. And if the email asks you to do things that don’t seem normal, like moving money to a different account, it’s a trick that hackers often use in spear phishing. They want to make you feel like you know them well and that what they’re asking is important. But it’s a way to get you to do things that could be risky.
By familiarizing ourselves with the red flags of phishing and the tactics cybercriminals employ, we take a step towards securing our online presence. Discover all four crucial security concepts that will empower you to protect yourself in our Security Awareness 101 [4 Concepts You Must Know] blog.
WATCH THE FULL WEBINAR
Discover the latest insights, best practices, and proactive measures that can safeguard you and your organization from potential threats. Watch our full Security Awareness 101 webinar now and take your security awareness to new heights with guidance from our seasoned professionals.
Are You Smarter Than a Phisher?
Play this game to see if you can outsmart the scammers!
You should not be worried whether you’re secure. Partner with Aldridge and become confident that you’re prepared for whatever happens next. Take a look at our IT Security page to see how we can help.







