Cybersecurity has significantly evolved over the past decade. Five to ten years ago, the primary focus was on antivirus software and protecting against malicious software intrusions. While these measures remain crucial components of a layered security approach, the nature of cyber threats has become more sophisticated. Today, businesses face a new threat known as live off the land cyber attacks. These attacks leverage existing tools and software within an organization’s environment, making them challenging to detect and prevent.
Trending Threat: Live off the Land (LOTL) Attacks
What Are Live Off the Land Cyber Attacks?
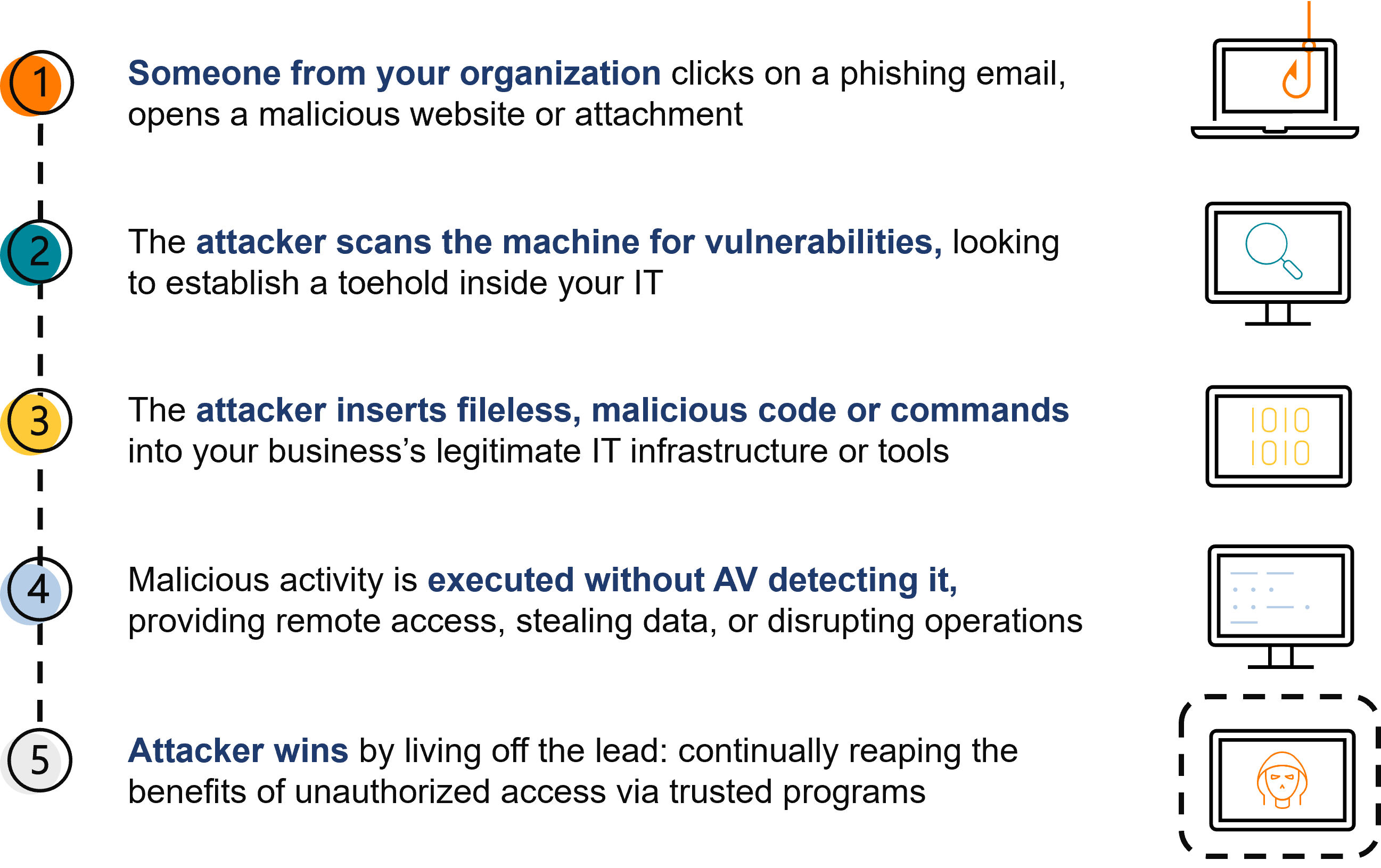
Live off the land techniques are not new, but their application has become more widespread and advanced. Unlike traditional attacks that rely on external malicious software, LOTL attacks use the tools and software already present in an organization’s IT infrastructure.
Threat actors use their expertise to manipulate these tools for malicious purposes. Essentially, they “live off the land,” using what’s available in the environment to carry out their attacks.
How Live off the Land Cyber Attacks Work
LOTL attacks typically begin with a common entry point, such as a compromised credential. Once inside the network, the attacker surveys the available tools and resources. These could include system administration utilities, scripting languages, and other legitimate software that employees use daily. By leveraging these tools, attackers can move laterally within the network, maintain a presence, and prepare for larger attacks targeting the organization’s data confidentiality, integrity, or availability.
Defending Against Live Off the Land Attacks
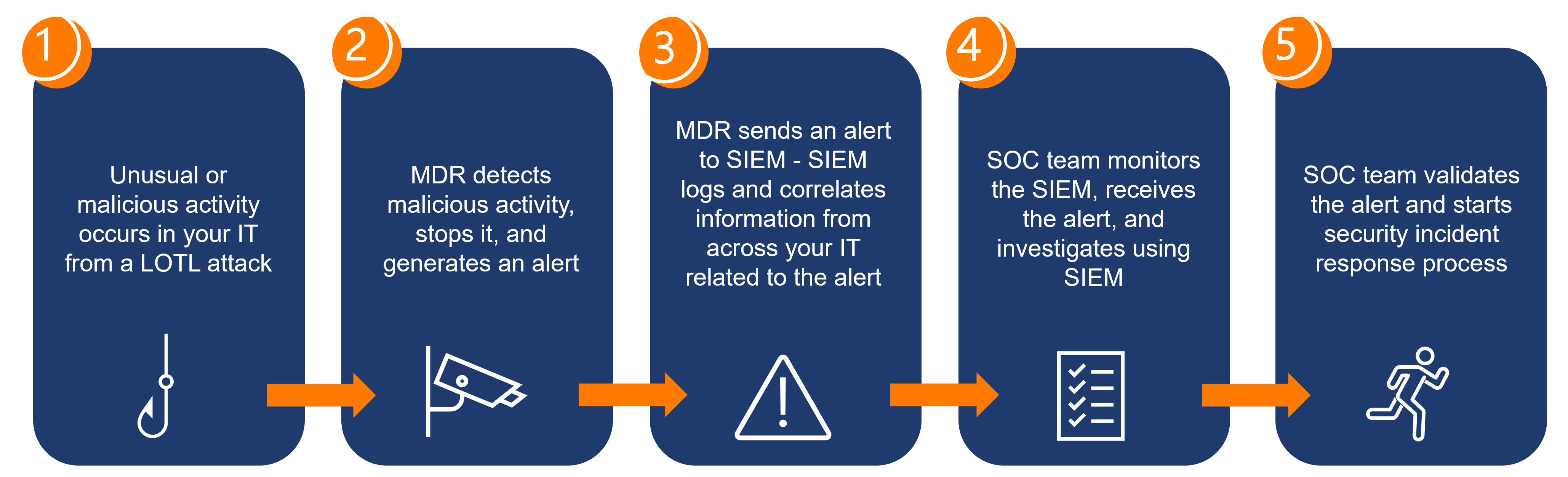
Defending against LOTL attacks requires a layered security approach, with Managed Detection and Response (MDR) playing an important role. MDR involves continuous monitoring and analysis of network activity to identify and respond to threats in real-time.
Modern MDR solutions go beyond detecting the execution of tools; they analyze the context and behavior surrounding their use. This analysis helps identify suspicious activities that stray from normal patterns, triggering security investigations.
Key Steps in MDR Defense
- Detection: MDR tools monitor network activity to detect the use of tools and software. They look for unusual patterns and behaviors that might indicate a LOTL attack.
- Investigation: Upon detecting suspicious activity, the MDR team investigates to determine the extent of the threat. This involves identifying who executed the tool, what actions were performed, and the initial point of entry.
- React: MDR sends an alert to SIEM (Security Information & Event Management) – SIEM then logs and correlates information from across your IT related to the alert.
- Response: Once a threat is confirmed, the MDR team acts swiftly to mitigate it. This includes stopping the malicious activity, preventing further damage, and identifying vulnerabilities that allowed the attack to occur.
- Forensics and Analysis: Post-incident, the team conducts a thorough analysis to understand how the attack happened, who was behind it, and what they were trying to achieve. This information is crucial for strengthening defenses and preventing future attacks.
Live off the land attacks represent a significant shift in how cyber threats are executed. By leveraging existing tools within an organization’s environment, these attacks are challenging to detect and mitigate. However, with a layered security approach that includes advanced MDR capabilities, businesses can effectively defend against these threats.
WATCH THE FULL VIDEO
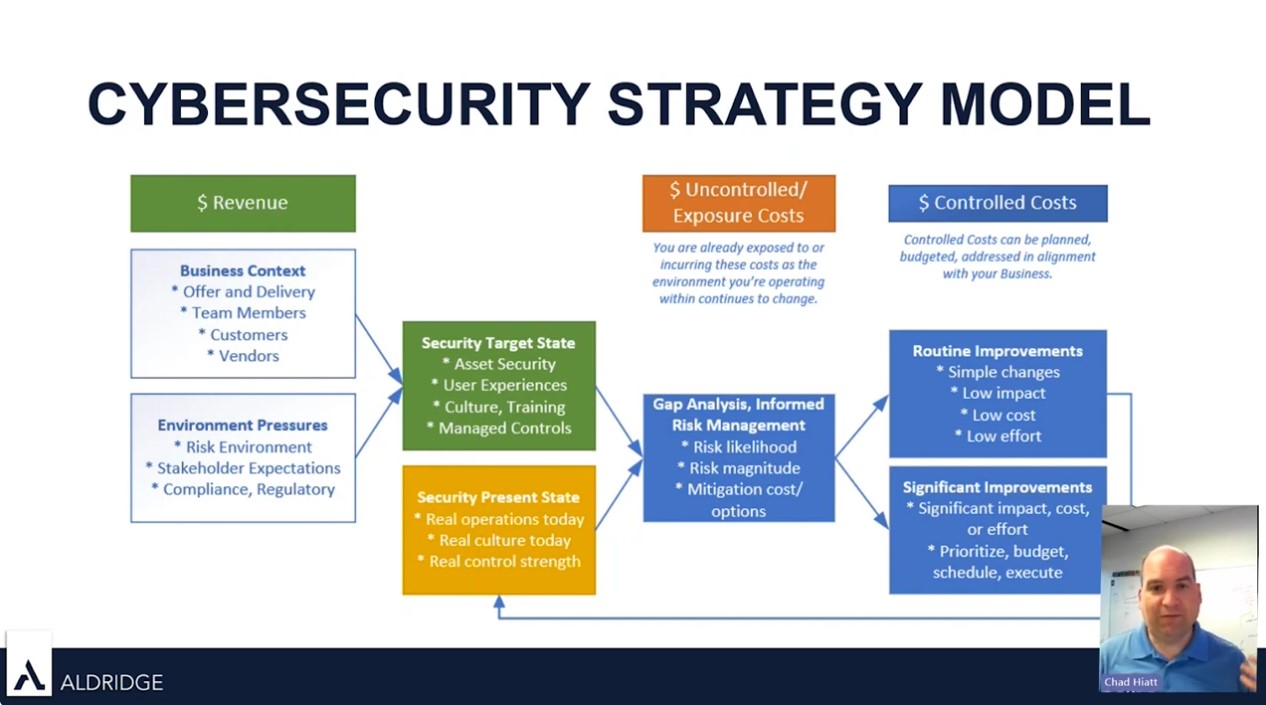
Aldridge’s CTO, Chad Hiatt, talks on cybersecurity updates and the ‘Right of Boom’ concept. Watch the full video to see how you should be thinking about security, gain valuable perspectives on the evolving LOTL threat landscape, learn about the new best security practices of 2024, and using a cybersecurity strategy model for success.