Aldridge Blog
Quick reads to improve your IT strategy
Most Recent Posts
SOC & SIEM Explained
Businesses of all sizes are vulnerable to cyber threats. To mitigate these risks, organizations rely on a Security Operations Center (SOC) and Security Information and Event Management (SIEM) system. What is SOC? A Security Operations Center (SOC) is a centralized...
Microsoft 365 App Exploit: Aldridge Cybersecurity Advisory
Recently, we've helped several organizations respond to a string of fast-paced phishing attacks. While phishing isn't new, the speed and tactics of these attacks were noteworthy. Instead of simply exploiting compromised accounts, the attacker installed malicious...
Why You Need SOC and SIEM for a Strong Cyber Defense
As cyberthreats continue to evolve, business leaders are increasingly turning to solutions like Security Operations Centers (SOC) and Security Information and Event Management (SIEM) to stay ahead. You’ve probably heard these terms before, and you might even be...
Reporting Phishing Emails in Microsoft Outlook
Phishing attacks are becoming increasingly commonplace; it's no longer a question of 'if', but 'when'. When you receive a phishing email, it's important that you understand how to recognize the attack and take the appropriate action. If you're a Microsoft Outlook...
How Cybercriminals Compromise Your Business Email
Email compromise is a clever and widespread technique used by cybercriminals to breach the security of both individuals and organizations, in fact, email compromise is the most common & costliest breach to date. Related | Email Compromise: The Most Common &...
How to Report Phishing Attacks the Right Way
The battle against phishing requires not only cautious online behavior but also an understanding of how to report phishing incidents effectively. Take a look at the crucial steps and strategies for reporting phishing the right way and safeguarding both your personal...
Protect Yourself from Phishing (5 Red Flags to Watch for)
Cybercriminals have perfected the art of deception, creating sophisticated traps that can trap even the most cautious of users. As we navigate the internet, it's crucial to arm ourselves with the knowledge and awareness necessary to recognize phishing attempts and...
Cybersecurity Hygiene: 6 Best Practices to Work Responsibly
Just as we prioritize personal hygiene to stay healthy, adopting a proactive approach to safeguarding our digital lives is equally important. The concept of “Cybersecurity Hygiene” takes practice and knowledge to fully master, but understanding these basic...
How Agile is Your Business? (3 levels)
You need to be agile to survive in today’s business landscape. In times of uncertainty, you must be ready to react to threats and capitalize on opportunities. There is a big difference between being agile, and simply reacting based on gut feelings. There are three...
How to Optimize Your Business Functions Around Your Value Proposition
Optimizing your business functions requires you to critically assess each function within your organization based on how it contributes to your core value proposition. An optimized business is agile; it can seize opportunities, overcome challenges, and consistently...
It Security
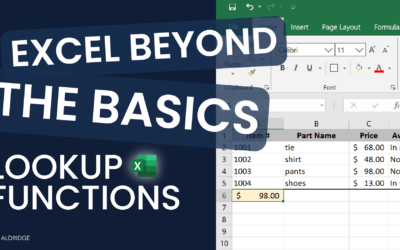
How to Use vLookup and xLookup Functions in Excel
Lookup functions in Excel simplify data retrieval by allowing users to search for specific information within datasets efficiently. How to Use vLookup and xLookup Functions in Excel vLookup The V in VLOOKUP stands for "Vertical." In Excel, the VLookup function...
How to Use Named Ranges in Microsoft Excel
Named ranges in Microsoft Excel simplify data management by assigning meaningful names to specific cell ranges, making formulas easier to understand and maintain. How to Use Named Ranges in Microsoft Excel You can use the labels of columns and rows on a worksheet to...
Managed IT Services for Dallas Financial Service Firms
Although Aldridge caters to a diverse array of businesses, our team has specific expertise for collaborating with Dallas financial service firms. We comprehend the complex IT challenges distinctive to this industry and offer the following specialized managed IT...
Microsoft 365
Pros and Cons of Microsoft 365 Business Premium
Microsoft 365 Business Premium is a subscription-based service that offers a wide range of tools and features to help businesses stay productive and organized. Take a look at some of the benefits and drawbacks of Microsoft 365 Business Premium. Pros and Cons of...
[Teams Tips] Using Loop Components to Collaborate Through Teams Chat
Loop components are a feature on Microsoft Teams that allow you to create interactive and dynamic content in your chat. These components can be used to create lists, discussion topics, tables, and other interactive elements that can engage your team members and...
[Teams Tips] How to Create & Use Microsoft Teams Tasks
Creating a task in Microsoft Teams is a great way to keep track of your to-do list and stay organized within your team. Here's how to do it: Create a Task in Microsoft Teams Open Microsoft Teams and hover over the message that you want to create the task for. Click on...
It Consulting
Why You Should be Using ‘Named Ranges’ in Excel
One of the most powerful yet often underutilized features in Excel is Named Ranges. Named Ranges offer significant benefits, especially when dealing with complex datasets and formulas. What Are Named Ranges? Named Ranges in Excel allow you to assign a name to a...
Microsoft 365 App Exploit: Aldridge Cybersecurity Advisory
Recently, we've helped several organizations respond to a string of fast-paced phishing attacks. While phishing isn't new, the speed and tactics of these attacks were noteworthy. Instead of simply exploiting compromised accounts, the attacker installed malicious...
Don’t Miss Our Most Popular Articles
How to Use vLookup and xLookup Functions in Excel
Lookup functions in Excel simplify data retrieval by allowing users to search for specific information within datasets efficiently. How to Use vLookup and xLookup Functions in Excel vLookup The V in VLOOKUP stands for "Vertical." In Excel, the VLookup function...
How to Use Named Ranges in Microsoft Excel
Named ranges in Microsoft Excel simplify data management by assigning meaningful names to specific cell ranges, making formulas easier to understand and maintain. How to Use Named Ranges in Microsoft Excel You can use the labels of columns and rows on a worksheet to...
Managed IT Services for Dallas Financial Service Firms
Although Aldridge caters to a diverse array of businesses, our team has specific expertise for collaborating with Dallas financial service firms. We comprehend the complex IT challenges distinctive to this industry and offer the following specialized managed IT...