Aldridge Blog
Quick reads to improve your IT strategy
Most Recent Posts
Aldridge Acquires Ranger Solutions
Further Expanding Managed IT & Cybersecurity Services in Dallas HOUSTON, TX, February 26, 2025 — Aldridge, a leading managed IT services provider, is excited to announce the successful acquisition of Ranger Solutions, a well-established IT service provider in...
The Latest Wave of Microsoft Copilot
Microsoft continues to push the boundaries of AI-powered productivity with its latest updates to Microsoft 365 Copilot. With over 150 new features and 700+ product updates this year, Microsoft has been focused on addressing the challenges many of us face in our daily...
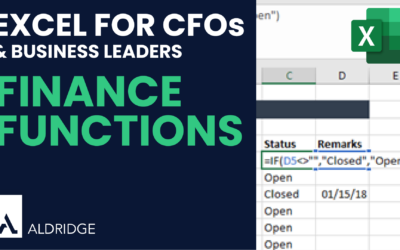
5 Advanced Excel Functions You Should Know
Excel is helpful for payroll analysis by leveraging powerful functions like SUM, SUBTOTAL, SUMIF, COUNTIF, and XLOOKUP. These formulas can help you analyze employee payroll data efficiently, even if you're starting from scratch or managing a simple spreadsheet. ...
How Agile is Your Business? (3 levels)
You need to be agile to survive in today’s business landscape. In times of uncertainty, you must be ready to react to threats and capitalize on opportunities. There is a big difference between being agile, and simply reacting based on gut feelings. There are three...
How to Optimize Your Business Functions Around Your Value Proposition
Optimizing your business functions requires you to critically assess each function within your organization based on how it contributes to your core value proposition. An optimized business is agile; it can seize opportunities, overcome challenges, and consistently...
How to Identify Your Value Proposition
Crafting a distinctive identity for your company is essential for achieving success. This identity, often referred to as your core value proposition, is the heart and soul of who you are and what you bring to the table. Identifying and practicing your core value...
Security Awareness 101 [4 Concepts You Must Know]
With cyber threats evolving constantly, it is essential for everyone to be well-versed in security awareness. The global cost of cybercrime in 2022 was $8.44 trillion and it is estimated to jump to $23.84 trillion in 2027. Source: Statista Cybersecurity Report Whether...
3 Ways to Secure your Microsoft PowerPoint Presentations
The convenience of digital presentations also comes with the responsibility of keeping your content secure. Whether you are a student, a business professional, or a creative individual, safeguarding your PowerPoint presentations from unauthorized access and potential...
How to Make a Picture Background in Microsoft Word
You can personalize your Word documents by setting a picture as the background. Whether you want to add a touch of creativity to your resume or make your document stand out, using an image as your background can add visual appeal to your documents. How to Make a...
How to Optimize Your Business Around Your Value Proposition
Your resources are finite, and you need to make sure you’re investing your time and energy into the functions that enable your core value proposition. Don’t get bogged down by your back-office. While it’s important that your internet works and you pay your bills on...
It Security
The Cost of a Security Breach for Long-Term Care Providers
You know who loves sensitive resident data? Cybercriminals. Unfortunately, long-term care facilities are like their favorite store to shoplift from. Because long-term care facilities possess sensitive resident data, they are prime targets. Regulatory fines on top of...
3 Top Complaints Long-Term Care Providers Have About Their IT
One of the top complaints long-term care providers have about their IT systems is poor usability. Providers need IT systems that are easy to use, intuitive, and can help streamline their workflows. Unfortunately, many IT systems in long-term care are overly complex...
Should a Long-Term Care Provider Outsource Their IT?
Technology plays a crucial role in the delivery of resident care and the management of facilities. One question that long-term care providers often ask themselves is whether they should outsource their IT services or handle them in-house. Should a Long-Term Care...
Microsoft 365
How to Set up and Use Microsoft 365 Multi-Factor Authentication
Multi-Factor Authentication (MFA) protects against unauthorized, potentially malicious people from accessing your account. MFA supplements the log-in process by requiring the user to provide at least one second factor – something they have (such as physical access to...
Change your Background on Microsoft Teams
Video calls are something we have become very familiar with. The beauty of video calls is that you can attend a meeting just about anywhere, whether that be in a home office, your kitchen, or maybe even at your local McDonald’s. Depending on who your video call is...
How Microsoft Intune Protects Your Data & Devices
Microsoft Intune gives you the ability to control how devices work with your organization's data. Intune is a cloud-based mobile device management (MDM) tool that allows your IT team to remotely deploy applications, apply business-standard settings, enforce security...
It Consulting
Building Excel Dashboards for Leaders
Dashboards in Excel provide a powerful solution for financial leaders, CFOs, and analysts to visualize and interpret data efficiently. What is a Dashboard in Excel? An Excel dashboard is a visual representation of key metrics and data insights presented in one...
The Latest Wave of Microsoft Copilot
Microsoft continues to push the boundaries of AI-powered productivity with its latest updates to Microsoft 365 Copilot. With over 150 new features and 700+ product updates this year, Microsoft has been focused on addressing the challenges many of us face in our daily...
Don’t Miss Our Most Popular Articles
The Cost of a Security Breach for Long-Term Care Providers
You know who loves sensitive resident data? Cybercriminals. Unfortunately, long-term care facilities are like their favorite store to shoplift from. Because long-term care facilities possess sensitive resident data, they are prime targets. Regulatory fines on top of...
3 Top Complaints Long-Term Care Providers Have About Their IT
One of the top complaints long-term care providers have about their IT systems is poor usability. Providers need IT systems that are easy to use, intuitive, and can help streamline their workflows. Unfortunately, many IT systems in long-term care are overly complex...
Should a Long-Term Care Provider Outsource Their IT?
Technology plays a crucial role in the delivery of resident care and the management of facilities. One question that long-term care providers often ask themselves is whether they should outsource their IT services or handle them in-house. Should a Long-Term Care...